南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Control Flow Integrity

最 Control Flow Integrity
Control Flow Integrity
最鲁 Outline ·Threat Model 。Control Flow Graph Control Flow Integrity basic implementation Build CFG Instrumentation Evaluation Security and Adversary ·Binary-CFI(CCFIR) - Introduce Implementation Context-Sensitive CFl Context Sensitivity Problems - Context Sensitivity Problems Shadow Call Stack RAP Context-Sensitive CFI 2
2 Outline • Threat Model • Control Flow Graph • Control Flow Integrity basic implementation – Build CFG – Instrumentation – Evaluation – Security and Adversary • Binary-CFI(CCFIR) – Introduce – Implementation – Context-Sensitive CFI • Context Sensitivity Problems – Context Sensitivity Problems – Shadow Call Stack – RAP – Context-Sensitive CFI
最鲁 Threat Model 3
Threat Model 3
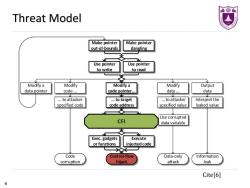
最鲁 Threat Model Make pointer Make pointer out-of-bounds dangling Use pointer Use pointer to write to read Modify a Modify Modify a Modify Output data pointer code... code pointer... data... data …to attacker ..to target ..to attacker Interpret the specified code code address specified value leaked value Use corrupted CFI data variable Exec.gadgets Execute or functions injected code Code Control-flow Data-only Information corruption hijack attack leak Cite[6] 4
4 Threat Model Cite[6]
最 Control Flow Graphs 5
Control Flow Graphs 5
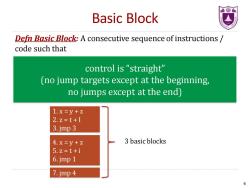
舍 Basic Block Defn Basic Block:A consecutive sequence of instructions/ code such that control is“straight'" (no jump targets except at the beginning, no jumps except at the end) 1.x=y+Z 2.z=t+I 3.jmp 3 4.x=y+Z 3 basic blocks 5.z=t+i 6.jmp 1 7.jmp 4 6
Defn Basic Block: A consecutive sequence of instructions / code such that • the instruction in each position always executes before (dominates) all those in later positions, and • no outside instruction can execute between two instructions in the sequence control is “straight” (no jump targets except at the beginning, no jumps except at the end) Basic Block 6 1. x = y + z 2. z = t + I 3. jmp 3 4. x = y + z 5. z = t + i 6. jmp 1 7. jmp 4 3 basic blocks

CFG Definition A static Control Flow Graph is a graph where each vertex v;is a basic block,and there is an edge (vi v)if there may be a transfer of control from block vi to block vi Historically,the scope of a "CFG"is limited to a function or procedure,i.e.,intra-procedural. 7
CFG Definition A static Control Flow Graphis a graph where – each vertex vi is a basic block, and – there is an edge (vi , vj ) if there may be a transfer of control from block vi to block vj . Historically, the scope of a “CFG” is limited to a function or procedure, i.e., intra-procedural. 7
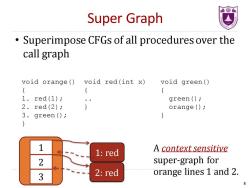
Super Graph Superimpose CFGs of all procedures over the call graph void orange() void red(int x) void green() { { { 1.red(1): green ( 2.red(2); orange () 3.green(); } 1 1:red A context sensitive 2 super-graph for 3 2:red orange lines 1 and 2. 8
Super Graph • Superimpose CFGs of all procedures over the call graph 1: red 1 2 3 2: red A context sensitive super-graph for orange lines 1 and 2. void orange() { 1. red(1); 2. red(2); 3. green(); } void red(int x) { .. } void green() { green(); orange(); } 8
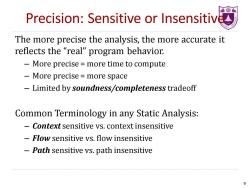
最需 Precision:Sensitive or Insensitiv The more precise the analysis,the more accurate it reflects the "real"program behavior. More precise more time to compute More precise more space Limited by soundness/completeness tradeoff Common Terminology in any Static Analysis: -Context sensitive vs.context insensitive Flow sensitive vs.flow insensitive Path sensitive vs.path insensitive 9
Precision: Sensitive or Insensitive The more precise the analysis, the more accurate it reflects the “real” program behavior. – More precise = more time to compute – More precise = more space – Limited by soundness/completeness tradeoff Common Terminology in any Static Analysis: – Context sensitive vs. context insensitive – Flow sensitive vs. flow insensitive – Path sensitive vs. path insensitive 9
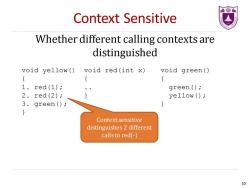
最剔 Context Sensitive Whether different calling contexts are distinguished void yellow()void red(int x) void green ( { { 1.red(1): green () 2.red(2); yellow(); 3.green(); Context sensitive distinguishes 2 different calls to red(-) 10
Context Sensitive Whether different calling contexts are distinguished void yellow() { 1. red(1); 2. red(2); 3. green(); } void red(int x) { .. } void green() { green(); yellow(); } Context sensitive distinguishes 2 different calls to red(-) 10
按次数下载不扣除下载券;
注册用户24小时内重复下载只扣除一次;
顺序:VIP每日次数-->可用次数-->下载券;
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Redundant dynamic Canary.ppt
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Defense against Control Flow Hijack Defense - StackGuard, DEP, and ASLR.pdf
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Buffer Overflow Attack.pdf
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Software Security Overview.pptx
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Introduction to the course.pdf
- 海南大学:《网络安全技术》课程教学资源(课件讲稿)第9章 入侵检测系统.pdf
- 海南大学:《网络安全技术》课程教学资源(课件讲稿)第8章 抗恶意软件.pdf
- 海南大学:《网络安全技术》课程教学资源(课件讲稿)第7章 网络边防.pdf
- 海南大学:《网络安全技术》课程教学资源(课件讲稿)第6章 无线网安全性.pdf
- 海南大学:《网络安全技术》课程教学资源(课件讲稿)第5章 实用的网络安全协议.pdf
- 海南大学:《网络安全技术》课程教学资源(课件讲稿)第3章 公钥密码体系与密钥管理.pdf
- 海南大学:《网络安全技术》课程教学资源(课件讲稿)第4章 数据认证.pdf
- 海南大学:《网络安全技术》课程教学资源(课件讲稿)第2章 数据加密算法.pdf
- 海南大学:《网络安全技术》课程教学资源(课件讲稿)第1章 网络安全概论(齐琦).pdf
- 电子科技大学:《数字图像处理》课程教学资源(课件讲稿)第十章 图像分割.pdf
- 电子科技大学:《数字图像处理》课程教学资源(课件讲稿)第五章 图像复原(图像几何校正).pdf
- 电子科技大学:《数字图像处理》课程教学资源(课件讲稿)第九章 形态学图像处理.pdf
- 电子科技大学:《数字图像处理》课程教学资源(课件讲稿)第六章 彩色图像处理.pdf
- 电子科技大学:《数字图像处理》课程教学资源(课件讲稿)第五章 图像复原.pdf
- 电子科技大学:《数字图像处理》课程教学资源(课件讲稿)第四章 频域图像增强.pdf
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Format String Attacks.pptx
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Return-Orinted Programming(ROP Attack).ppt
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Control Flow - Representation, Extraction and Applications.pptx
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Program Analysis - Data Flow Analysis.pptx
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Taint Analysis.pptx
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Use-after-free.pptx
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Byzantine Generals Problem.ppt
- 南京大学:《形式语言与自动机 Formal Languages and Automata》课程教学资源(PPT课件讲稿)Finite Automata.pptx
- 南京大学:《形式语言与自动机 Formal Languages and Automata》课程教学资源(PPT课件讲稿)Context Free Grammar.pptx
- 南京大学:《形式语言与自动机 Formal Languages and Automata》课程教学资源(PPT课件讲稿)Regular Expression.pptx
- 南京大学:《形式语言与自动机 Formal Languages and Automata》课程教学资源(PPT课件讲稿)Pushdown Automata.pptx
- 南京大学:《形式语言与自动机 Formal Languages and Automata》课程教学资源(PPT课件讲稿)Properties of CFL(The Pumping Lemma for CFL’s).pptx
- 南京大学:《形式语言与自动机 Formal Languages and Automata》课程教学资源(PPT课件讲稿)Turing Machine.pptx
- 南京大学:《形式语言与自动机 Formal Languages and Automata》课程教学资源(PPT课件讲稿)Transition System.pptx
- 南京大学:《形式语言与自动机 Formal Languages and Automata》课程教学资源(PPT课件讲稿)Petri Net.pptx
- 南京大学:《形式语言与自动机 Formal Languages and Automata》课程教学资源(PPT课件讲稿)Timed Automata.ppt
- 南京大学:《形式语言与自动机 Formal Languages and Automata》课程教学资源(PPT课件讲稿)Decidability, Complexity(P, NP, NPC and related).pptx
- 《大数据 Big Data》课程教学资源(参考文献)Learning to Hash for Big Data Retrieval and Mining(南京大学:李武军).pdf
- 《大数据 Big Data》课程教学资源(参考文献)Learning to Hash for Big Data Retrieval and Mining(南京大学:李武军).pdf
- 《大数据 Big Data》课程教学资源(参考文献)大数据机器学习 Big Data Machine Learning.pdf
