南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Software Security Overview

Software Security Overview Mao Bing Department of Computer Science NanJing University
Software Security Overview Mao Bing Department of Computer Science NanJing University

Outline ·Background 。 Software Security:Control-flow Hijack Attack Memory Layout,Stack frame,Procedure >Buffer Overflow:Vulnerability,Defenses RILC,Return-Oriented Programming ASLR CFI Software Security:Non-control Data Attack Data Oriented Programming ·Summary 2
2 Outline • Background • Software Security: Control-flow Hijack Attack ➢ Memory Layout , Stack frame, & Procedure ➢ Buffer Overflow: Vulnerability, & Defenses ➢ RILC, Return-Oriented Programming ➢ ASLR & CFI • Software Security: Non-control Data Attack ➢ Data Oriented Programming • Summary
Outline ·Background Software Security:Control-flow Hijack Attack Memory Layout,Stack frame,Procedure Buffer Overflow:Vulnerability,Defenses RILC,Return-Oriented Programming ASLR CFI Software Security:Non-control Data Attack Data Oriented Programming Summary 3
3 Outline • Background • Software Security: Control-flow Hijack Attack ➢ Memory Layout , Stack frame, & Procedure ➢ Buffer Overflow: Vulnerability, & Defenses ➢ RILC, Return-Oriented Programming ➢ ASLR & CFI • Software Security: Non-control Data Attack ➢ Data Oriented Programming • Summary
Computer Security Computer security,also known as cybersecurity or IT security,is the "...protection of information systems from theft(secrecy/confidentiality) or damage (integrity)to the 取7Y hardware,the software,and This picture is from http: to the information on them,..." //securitygem.com/home-security-reviews -Gasser,Morrie(1988)
4 Computer Security Computer security, also known as cybersecurity or IT security, is the “...protection of information systemsfrom theft(secrecy/confidentiality) or damage (integrity) to the hardware, the software, and to the information on them, ...” —Gasser, Morrie (1988)
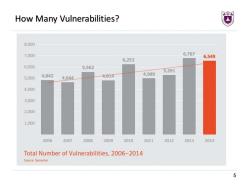
How Many Vulnerabilities? 8,000 7,000 6,787 6,549 6,253 6.000 5,562 5,291 4.989 5.000 4,842 4.644. 4814 4.000 3.000 2.000 1.000 2006 2007 2008 2009 2010 2011 2012 2013 2014 Total Number of Vulnerabilities,2006-2014 Source:Symantec 5
5 How Many Vulnerabilities?
Before Morris Worm,Computer Security is: Encryption Decryption Access Control ·DAC ·MAC ·Logic Bomb Back Door 6
6 Before Morris Worm, Computer Security is: • Encryption & Decryption • Access Control • DAC • MAC • Logic Bomb • Back Door
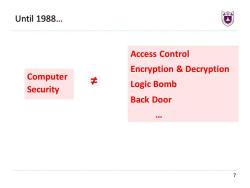
Until 1988... Access Control Encryption Decryption Computer Security Logic Bomb Back Door
7 Until 1988… Access Control Encryption & Decryption Logic Bomb Back Door … Computer Security ≠
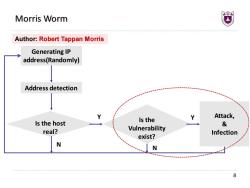
Morris Worm Author:Robert Tappan Morris Generating IP address(Randomly) Address detection Y Attack, Is the host Is the & real? Vulnerability Infection exist? N N 8
8 Morris Worm Generating IP address(Randomly) Address detection Is the host real? Is the Vulnerability exist? Attack, & Infection Y Y N N Author: Robert Tappan Morris

Morris Worm Vulnerability:Buffer Overflow Attack Infection Hijack control flow execute SHELLCODE Add the virus to the head or tail of the program 9
9 Morris Worm • Vulnerability: Buffer Overflow • Attack & Infection • Hijack control flow & execute SHELLCODE • Add the virus to the head or tail of the program
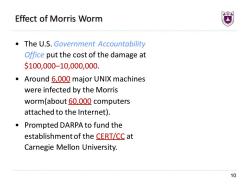
Effect of Morris Worm The U.S.Government Accountability Office put the cost of the damage at $100,000-10,000,000. Around 6,000 major UNIX machines were infected by the Morris worm(about 60,000 computers attached to the Internet). Prompted DARPA to fund the establishment of the CERT/CC at Carnegie Mellon University 10
10 Effect of Morris Worm • The U.S. Government Accountability Office put the cost of the damage at $100,000–10,000,000. • Around 6,000 major UNIX machines were infected by the Morris worm(about 60,000 computers attached to the Internet). • Prompted DARPA to fund the establishment of the CERT/CC at Carnegie Mellon University
按次数下载不扣除下载券;
注册用户24小时内重复下载只扣除一次;
顺序:VIP每日次数-->可用次数-->下载券;
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Introduction to the course.pdf
- 海南大学:《网络安全技术》课程教学资源(课件讲稿)第9章 入侵检测系统.pdf
- 海南大学:《网络安全技术》课程教学资源(课件讲稿)第8章 抗恶意软件.pdf
- 海南大学:《网络安全技术》课程教学资源(课件讲稿)第7章 网络边防.pdf
- 海南大学:《网络安全技术》课程教学资源(课件讲稿)第6章 无线网安全性.pdf
- 海南大学:《网络安全技术》课程教学资源(课件讲稿)第5章 实用的网络安全协议.pdf
- 海南大学:《网络安全技术》课程教学资源(课件讲稿)第3章 公钥密码体系与密钥管理.pdf
- 海南大学:《网络安全技术》课程教学资源(课件讲稿)第4章 数据认证.pdf
- 海南大学:《网络安全技术》课程教学资源(课件讲稿)第2章 数据加密算法.pdf
- 海南大学:《网络安全技术》课程教学资源(课件讲稿)第1章 网络安全概论(齐琦).pdf
- 电子科技大学:《数字图像处理》课程教学资源(课件讲稿)第十章 图像分割.pdf
- 电子科技大学:《数字图像处理》课程教学资源(课件讲稿)第五章 图像复原(图像几何校正).pdf
- 电子科技大学:《数字图像处理》课程教学资源(课件讲稿)第九章 形态学图像处理.pdf
- 电子科技大学:《数字图像处理》课程教学资源(课件讲稿)第六章 彩色图像处理.pdf
- 电子科技大学:《数字图像处理》课程教学资源(课件讲稿)第五章 图像复原.pdf
- 电子科技大学:《数字图像处理》课程教学资源(课件讲稿)第四章 频域图像增强.pdf
- 电子科技大学:《数字图像处理》课程教学资源(课件讲稿)第三章 空间域图像增强.pdf
- 电子科技大学:《数字图像处理》课程教学资源(课件讲稿)第二章 数字图像处理基础.pdf
- 电子科技大学:《数字图像处理》课程教学资源(课件讲稿)第一章 绪论 Digital Image Processing(主讲:于力).pdf
- 海南大学:《信息安全导论 Introduction to Information Security》课程教学资源(课件讲稿)第12章 信息安全管理与审计.pdf
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Buffer Overflow Attack.pdf
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Defense against Control Flow Hijack Defense - StackGuard, DEP, and ASLR.pdf
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Redundant dynamic Canary.ppt
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Control Flow Integrity.pptx
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Format String Attacks.pptx
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Return-Orinted Programming(ROP Attack).ppt
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Control Flow - Representation, Extraction and Applications.pptx
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Program Analysis - Data Flow Analysis.pptx
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Taint Analysis.pptx
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Use-after-free.pptx
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Byzantine Generals Problem.ppt
- 南京大学:《形式语言与自动机 Formal Languages and Automata》课程教学资源(PPT课件讲稿)Finite Automata.pptx
- 南京大学:《形式语言与自动机 Formal Languages and Automata》课程教学资源(PPT课件讲稿)Context Free Grammar.pptx
- 南京大学:《形式语言与自动机 Formal Languages and Automata》课程教学资源(PPT课件讲稿)Regular Expression.pptx
- 南京大学:《形式语言与自动机 Formal Languages and Automata》课程教学资源(PPT课件讲稿)Pushdown Automata.pptx
- 南京大学:《形式语言与自动机 Formal Languages and Automata》课程教学资源(PPT课件讲稿)Properties of CFL(The Pumping Lemma for CFL’s).pptx
- 南京大学:《形式语言与自动机 Formal Languages and Automata》课程教学资源(PPT课件讲稿)Turing Machine.pptx
- 南京大学:《形式语言与自动机 Formal Languages and Automata》课程教学资源(PPT课件讲稿)Transition System.pptx
- 南京大学:《形式语言与自动机 Formal Languages and Automata》课程教学资源(PPT课件讲稿)Petri Net.pptx
- 南京大学:《形式语言与自动机 Formal Languages and Automata》课程教学资源(PPT课件讲稿)Timed Automata.ppt
