南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Byzantine Generals Problem

Background: Distributed Systems Synchronization/Logical time/Happens-before Consistency(Asynchronized Communication) Fault Tolerance(redundancy/k fault tolerant) distributed consensus
Background: Distributed Systems Synchronization/Logical time/Happens-before Consistency( Asynchronized Communication) Fault Tolerance(redundancy/k fault tolerant) distributed consensus

Problem description(distributed consensus) Consider a set of n isolated processors,of which it is known t that no more than m are faulty.It is not known,however,which processors are faulty.Suppose that the processors can commumcate only by means of two-party messages.The communication medium is presumed to be fail-safe and of negligible delay.The sender of a message,moreover,is always identifiable by the receiver.Suppose also that each processor p has some private value of information Vp(such as its clock value or its reading of some sensor). The question is whether for given m,n>0,it is possible to devise an algorithm based on an exchange of messages that will allow each nonfaulty processor)to compute a vector of values with an element for each of the n processors,such that
Problem description(distributed consensus) Consider a set of n isolated processors, of which it is known that no more than m are faulty. It is not known, however, which processors are faulty. Suppose that the processors can commumcate only by means of two-party messages. The communication medium is presumed to be fail-safe and of negligible delay. The sender of a message, moreover, is always identifiable by the receiver. Suppose also that each processor p has some private value of information Vp (such as its clock value or its reading of some sensor). The question is whether for given m, n > 0, it is possible to devise an algorithm based on an exchange of messages that will allow each nonfaulty processor) to compute a vector of values with an element for each of the n processors, such that

(1)the nonfaulty processors compute exactly the same vector, (2)the element of this vector corresponding to a given nonfaulty processor is the private value of that processor Interactive Consistency(IC)
(1) the nonfaulty processors compute exactly the same vector; (2) the element of this vector corresponding to a given nonfaulty processor is the private value of that processor. Interactive Consistency(IC)

The generals must have an algorithm to guarantee that: A.All loyal generals decide upon the same plan of action. A small number of traitors cannot cause the loyal generals to adopt a bad plan
The generals must have an algorithm to guarantee that: • A. All loyal generals decide upon the same plan of action. • A small number of traitors cannot cause the loyal generals to adopt a bad plan

For condition A to be satisfied,the following must be true: 1.Every loyal general must obtain the same information v (1)....,v (n). 2.If the ith general is loyal,then the value that he sends must be used by every loyal general as the value of v (i)
For condition A to be satisfied, the following must be true: • 1. Every loyal general must obtain the same information v (1) . . . . , v (n). • 2. If the ith general is loyal, then the value that he sends must be used by every loyal general as the value of v (i)

We can rewrite condition I as the condition that for every i (whether or not the ith general is loyal): 1'.Any two loyal generals use the same value of v(i)
We can rewrite condition I as the condition that for every i (whether or not the ith general is loyal): • 1'. Any two loyal generals use the same value of v(i)

Byzantine Generals Problem. A commanding general must send an order to his n-1 lieutenant generals such that IC1.All loyal lieutenants obey the same order. IC2.If the commanding general is loyal, then every loyal lieutenant obeys the order he sends
• Byzantine Generals Problem. A commanding general must send an order to his n - 1 lieutenant generals such that • IC1. All loyal lieutenants obey the same order. • IC2. If the commanding general is loyal, then every loyal lieutenant obeys the order he sends

n processes,m faulty n3m m+1 rounds/intuition perceptual knowledge/examples algorithms proofs
n processes, m faulty n3m m+1 rounds/intuition perceptual knowledge/examples algorithms proofs

Examples: m=1,n=3/4 m=2,n=6/7
Examples: m=1, n=3/4 m=2, n=6/7
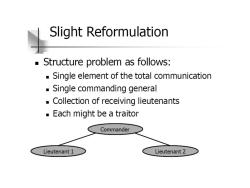
Slight Reformulation Structure problem as follows: Single element of the total communication Single commanding general Collection of receiving lieutenants Each might be a traitor Commander Lieutenant 1 Lieutenant 2
按次数下载不扣除下载券;
注册用户24小时内重复下载只扣除一次;
顺序:VIP每日次数-->可用次数-->下载券;
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Use-after-free.pptx
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Taint Analysis.pptx
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Program Analysis - Data Flow Analysis.pptx
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Control Flow - Representation, Extraction and Applications.pptx
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Return-Orinted Programming(ROP Attack).ppt
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Format String Attacks.pptx
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Control Flow Integrity.pptx
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Redundant dynamic Canary.ppt
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Defense against Control Flow Hijack Defense - StackGuard, DEP, and ASLR.pdf
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Buffer Overflow Attack.pdf
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Software Security Overview.pptx
- 南京大学:《软件安全 Software Security》课程教学资源(PPT课件讲稿)Introduction to the course.pdf
- 海南大学:《网络安全技术》课程教学资源(课件讲稿)第9章 入侵检测系统.pdf
- 海南大学:《网络安全技术》课程教学资源(课件讲稿)第8章 抗恶意软件.pdf
- 海南大学:《网络安全技术》课程教学资源(课件讲稿)第7章 网络边防.pdf
- 海南大学:《网络安全技术》课程教学资源(课件讲稿)第6章 无线网安全性.pdf
- 海南大学:《网络安全技术》课程教学资源(课件讲稿)第5章 实用的网络安全协议.pdf
- 海南大学:《网络安全技术》课程教学资源(课件讲稿)第3章 公钥密码体系与密钥管理.pdf
- 海南大学:《网络安全技术》课程教学资源(课件讲稿)第4章 数据认证.pdf
- 海南大学:《网络安全技术》课程教学资源(课件讲稿)第2章 数据加密算法.pdf
- 南京大学:《形式语言与自动机 Formal Languages and Automata》课程教学资源(PPT课件讲稿)Finite Automata.pptx
- 南京大学:《形式语言与自动机 Formal Languages and Automata》课程教学资源(PPT课件讲稿)Context Free Grammar.pptx
- 南京大学:《形式语言与自动机 Formal Languages and Automata》课程教学资源(PPT课件讲稿)Regular Expression.pptx
- 南京大学:《形式语言与自动机 Formal Languages and Automata》课程教学资源(PPT课件讲稿)Pushdown Automata.pptx
- 南京大学:《形式语言与自动机 Formal Languages and Automata》课程教学资源(PPT课件讲稿)Properties of CFL(The Pumping Lemma for CFL’s).pptx
- 南京大学:《形式语言与自动机 Formal Languages and Automata》课程教学资源(PPT课件讲稿)Turing Machine.pptx
- 南京大学:《形式语言与自动机 Formal Languages and Automata》课程教学资源(PPT课件讲稿)Transition System.pptx
- 南京大学:《形式语言与自动机 Formal Languages and Automata》课程教学资源(PPT课件讲稿)Petri Net.pptx
- 南京大学:《形式语言与自动机 Formal Languages and Automata》课程教学资源(PPT课件讲稿)Timed Automata.ppt
- 南京大学:《形式语言与自动机 Formal Languages and Automata》课程教学资源(PPT课件讲稿)Decidability, Complexity(P, NP, NPC and related).pptx
- 《大数据 Big Data》课程教学资源(参考文献)Learning to Hash for Big Data Retrieval and Mining(南京大学:李武军).pdf
- 《大数据 Big Data》课程教学资源(参考文献)Learning to Hash for Big Data Retrieval and Mining(南京大学:李武军).pdf
- 《大数据 Big Data》课程教学资源(参考文献)大数据机器学习 Big Data Machine Learning.pdf
- 《大数据 Big Data》课程教学资源(参考文献)Learning to Hash for Big Data.pdf
- 《大数据 Big Data》课程教学资源(参考文献)Learning to Hash for Big Data.pdf
- 《大数据 Big Data》课程教学资源(参考文献)大数据机器学习 Big Data Machine Learning.pdf
- 《大数据 Big Data》课程教学资源(参考文献)Learning to Hash for Big Data - A Tutorial.pdf
- 《大数据 Big Data》课程教学资源(参考文献)Parallel and Distributed Stochastic Learning - Towards Scalable Learning for Big Data Intelligence(南京大学:李武军).pdf
- 《人工智能、机器学习与大数据》课程教学资源(参考文献)Coherence functions for multicategory margin-based classification methods.pdf
- 《人工智能、机器学习与大数据》课程教学资源(参考文献)Latent Wishart processes for relational kernel learning.pdf
