南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)19 Firewall Design Methods

Firewall Design Methods Haipeng Dai haipengdai@nju.edu.cn 313 CS Building Department of Computer Science and Technology Nanjing University
Firewall Design Methods Haipeng Dai haipengdai@nju.edu.cn 313 CS Building Department of Computer Science and Technology Nanjing University

Security Guard for Private Buildings 5G0 2
2 Security Guard for Private Buildings
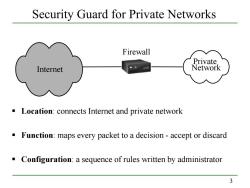
Security Guard for Private Networks Firewall Private. Internet Network Location:connects Internet and private network Function:maps every packet to a decision-accept or discard Configuration:a sequence of rules written by administrator 3
3 Security Guard for Private Networks Location: connects Internet and private network Function: maps every packet to a decision - accept or discard Configuration: a sequence of rules written by administrator Internet Private Network Firewall
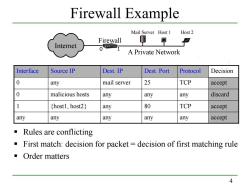
Firewall Example Mail Server Host 1 Host 2 Firewall Internet A Private Network Interface Source IP Dest.IP Dest.Port Protocol Decision 0 any mail server 25 TCP accept 0 malicious hosts any any any discard host1,host2) any 80 TCP accept any any any any any accept Rules are conflicting First match:decision for packet=decision of first matching rule ■Order matters 4
4 Firewall Example Interface Source IP Dest. IP Dest. Port Protocol Decision 0 any mail server 25 TCP accept 0 malicious hosts any any any discard 1 {host1, host2} any 80 TCP accept any any any any any accept Internet Firewall 0 1 Mail Server Host 1 Host 2 A Private Network Rules are conflicting First match: decision for packet = decision of first matching rule Order matters

Real-life Firewalls are Complex 523:conduit pernit tep host 100.77.28.87 eq 8100 any 524:conduit pernit tcp host 100.77.28.87 eq 8110 any Number of rules can be large 525:conduit pernit tcp host 100.77.28.84 eq ftp host 207.115.175.244 526:conduit pernit tcp host 100.77.28.84 eq telnet host 198.215.163.20 527:conduit pernit tep host 100.77.28.84 eq ftp host 198.215.163.20 Legacy rules 528:conduit pernit tep host 100.77.28.84 eq telnet host 198.215.163.21 529:conduit permit tep host 100.77.28.84 eq ftp host 198.215.163.21 530:conduit pernit tcp host 100.77.28.87 eq www host 207.115.175.244 Cascade impact of change 531:conduit pernit tcp host 100.77.28.87 eq telnet host 207.115.175.244 532:conduit pernit tcp ho3t100.77.28.87eq443ho3t207.115.175.244 533:conduit pernit tep host 100.77.28.87 eq ftp host 207.115.175.244 534:conduit pernit tep host 100.77.28.87 eq www host 205.170.235.0 535:conduit pernit tcp host 100.77.28.87 eq 443 host 205.170.235.0 536:conduit pernit tep host 100.77.28.87 eq ftp host 198.215.163.20 537:conduit permit tcp host 100.77.28.87 eq ftp host 198.215.163.21 538:conduit pernit tcp host 100.77.28.88 eq telnet 12.20.51.0 255.255.255.0 539:conduit permit tcp host100.77.28.88 eq ftp12.20.51.0255.255.255.0 540:conduit pernit tcp host100.77.28.88 eq www12.20.51.0255.255.255.0 541:conduit pernit tcp hos3t100.77.28.88eg1329212.20.51.0255.255.255.0 542:conduit pernit tcp host100.77.28.88eq44312.20.51.0255.255.255.0 543:conduit pernit tcp host 100.77.28.84 eq telnet 12.20.51.0 255.255.255.0 544:conduit permit tep host100.77.28.84 eq ftp12.20.51.0255.255.255.0 545:conduit pernit tcp ho3t100.77.28.85 eq wwnw12.20.51.0255.255.255.0 546:conduit permit tcp host 100.77.28.85 eq telnet 12.20.51.0 255.255.255.0 547:conduit pernit tcp host100.77.28.85eq44312.20.51.0255.255.255.0 548:conduit pernit tcp host100.77.28.85 eq ftp12.20.51.0255.255.255.0 549:conduit permit tcp host100.77.28.87eqnw12.20.51.0255.255.255.0 550:conduit pernit tcp host 100.77.28.87 eq telnet 12.20.51.0 255.255.255.0 5E1.i+++100 77 29 97443 19 90 E1 0 255255 O55 n 5
5 Real-life Firewalls are Complex Number of rules can be large Legacy rules Cascade impact of change

Problem As a result,firewall rules are hard to specify correctly hard to understand correctly hard to change correctly ■ Consequently,firewall configuration errors are common -Most firewalls are poorly designed with errors [Wool04] Firewall errors are unacceptable -Accept malicious packets:lose security -Discard legitimate packets:disrupt business Problem:How to design firewalls? 6
6 Problem As a result, firewall rules are hard to specify correctly hard to understand correctly hard to change correctly Consequently, firewall configuration errors are common ─ Most firewalls are poorly designed with errors [Wool'04] Firewall errors are unacceptable ─ Accept malicious packets: lose security ─ Discard legitimate packets: disrupt business Problem: How to design firewalls?
State-of-the-art Industry:tweak and pray “God bless my rules" Academia:analyze rules -Such as conflict detection ([HSP 00][EM 01][BV 02]) anomaly detection ([AH 03][AH 041) 7
7 State-of-the-art Industry: tweak and pray Academia: analyze rules ─ Such as conflict detection ([HSP 00] [EM 01] [BV 02]) anomaly detection ([AH 03] [AH 04]) “God bless my rules

Structured Firewall Design:Motivation The convention of designing a firewall directly as a sequence of conflicting rules has been taken for granted We point out that this convention is BAD. Why:this convention has three major issues -Consistency issue Completeness issue -Compactness issue 8
8 Structured Firewall Design: Motivation The convention of designing a firewall directly as a sequence of conflicting rules has been taken for granted We point out that this convention is BAD. Why: this convention has three major issues ─ Consistency issue ─ Completeness issue ─ Compactness issue

Consistency Issue Interface Source IP Dest.IP Dest.Port Protocol Decision 0 any mail server 25 TCP accept 0 malicious hosts any any any discard host1,host2) any 80 TCP accept any any any any any accept This firewall accepts email from malicious hosts! This is wrong(assuming this firewall is required to discard all packets from malicious hosts) 9
9 Consistency Issue This firewall accepts email from malicious hosts! This is wrong (assuming this firewall is required to discard all packets from malicious hosts) Interface Source IP Dest. IP Dest. Port Protocol Decision 0 any mail server 25 TCP accept 0 malicious hosts any any any discard 1 {host1, host2} any 80 TCP accept any any any any any accept
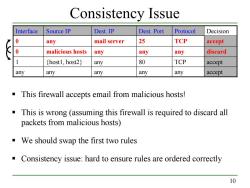
Consistency Issue Interface Source IP Dest.IP Dest.Port Protocol Decision 0 any mail server 25 TCP accept 0 malicious hosts any any any discard host1,host2) any 80 TCP accept any any any any any accept This firewall accepts email from malicious hosts! This is wrong (assuming this firewall is required to discard all packets from malicious hosts) We should swap the first two rules Consistency issue:hard to ensure rules are ordered correctly 10
10 Consistency Issue This firewall accepts email from malicious hosts! This is wrong (assuming this firewall is required to discard all packets from malicious hosts) We should swap the first two rules Consistency issue: hard to ensure rules are ordered correctly Interface Source IP Dest. IP Dest. Port Protocol Decision 0 any mail server 25 TCP accept 0 malicious hosts any any any discard 1 {host1, host2} any 80 TCP accept any any any any any accept
按次数下载不扣除下载券;
注册用户24小时内重复下载只扣除一次;
顺序:VIP每日次数-->可用次数-->下载券;
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)18 Web Security(SQL Injection and Cross-Site Request Forgery).pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)17 Web Security(Cookies and Cross Site Scripting,XSS).pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)16 Bloom Filter for Network Security.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)15 Bloom Filters and its Variants.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)14 Buffer Overflow Attacks.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)13 Human Authentication.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)12 Secure Socket Layer(SSL)、TLS(Transport Layer Security).pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)11 Public-Key Infrastructure.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)10 Kerberos.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)09 Authentication Using Symmetric Keys.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)08 Authentication Using Asymmetric Keys.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)07 Hashes and Message Digests.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)06 Number Theory.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)05 Asymmetric Key Cryptography.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)04 Advanced Encryption Standard(AES).pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)03 Symmetric Key Cryptography.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)02 Security Principles.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)01 Introduction(戴海鹏).pdf
- 南京大学:《Java语言程序设计 Programming in Java》课程教学资源(教案讲义)Lecture 09 图形用户界面的设计与实现.ppt
- 南京大学:《Java语言程序设计 Programming in Java》课程教学资源(教案讲义)Lecture 08 数据结构与算法.ppt
- 《GPU并行编程 GPU Parallel Programming》课程教学资源(参考文献)MPI A Message-Passing Interface Standard(Version 2.2).pdf
- 《GPU并行编程 GPU Parallel Programming》课程教学资源(参考文献)An Asymmetric Distributed Shared Memory Model for Heterogeneous Parallel Systems.pdf
- 《GPU并行编程 GPU Parallel Programming》课程教学资源(参考文献)Software and the Concurrency Revolution.pdf
- 《GPU并行编程 GPU Parallel Programming》课程教学资源(参考文献)Some Computer Organizations and Their Effectiveness.pdf
- 《GPU并行编程 GPU Parallel Programming》课程教学资源(参考文献)Optimization Principles and Application Performance Evaluation of a Multithreaded GPU Using CUDA.pdf
- 《GPU并行编程 GPU Parallel Programming》课程教学资源(参考文献)Program Optimization Space Pruning for a Multithreaded GPU.pdf
- 《GPU并行编程 GPU Parallel Programming》课程教学资源(参考文献)Single-pass Parallel Prefix Scan with Decoupled Look-back.pdf
- 《GPU并行编程 GPU Parallel Programming》课程教学资源(参考文献)NVIDIA Parallel Prefix Sum(Scan)with CUDA(April 2007).pdf
- 《GPU并行编程 GPU Parallel Programming》课程教学资源(参考文献)Methods of conjugate gradients for solving linear systems.pdf
- 《GPU并行编程 GPU Parallel Programming》课程教学资源(参考文献)NVIDIA CUDA C Programming Guide(Design Guide,June 2017).pdf
- 电子科技大学:《GPU并行编程 GPU Parallel Programming》课程教学资源(课件讲稿)Lecture 01 Introduction To Cuda C.pdf
- 电子科技大学:《GPU并行编程 GPU Parallel Programming》课程教学资源(课件讲稿)Lecture 02 CUDA PARALLELISM MODEL.pdf
- 电子科技大学:《GPU并行编程 GPU Parallel Programming》课程教学资源(课件讲稿)Lecture 03 MEMORY AND DATA LOCALITY.pdf
- 电子科技大学:《GPU并行编程 GPU Parallel Programming》课程教学资源(课件讲稿)Lecture 04 Performance considerations.pdf
- 电子科技大学:《GPU并行编程 GPU Parallel Programming》课程教学资源(课件讲稿)Lecture 05 PARALLEL COMPUTATION PATTERNS(HISTOGRAM).pdf
- 电子科技大学:《GPU并行编程 GPU Parallel Programming》课程教学资源(课件讲稿)Lecture 06 PARALLEL COMPUTATION PATTERNS(SCAN).pdf
- 电子科技大学:《GPU并行编程 GPU Parallel Programming》课程教学资源(课件讲稿)Lecture 07 JOINT CUDA-MPI PROGRAMMING.pdf
- 电子科技大学:《GPU并行编程 GPU Parallel Programming》课程教学资源(课件讲稿)Lecture 08 Parallel Sparse Methods.pdf
- 电子科技大学:《GPU并行编程 GPU Parallel Programming》课程教学资源(课件讲稿)Lecture 09 Parallel patterns(MERGE SORT).pdf
- 电子科技大学:《GPU并行编程 GPU Parallel Programming》课程教学资源(课件讲稿)Lecture 10 Computational Thinking.pdf
