南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)09 Authentication Using Symmetric Keys

Authentication Using Symmetric Keys Haipeng Dai haipengdai@nju.edu.cn 313 CS Building Department of Computer Science and Technology Nanjing University
Authentication Using Symmetric Keys Haipeng Dai haipengdai@nju.edu.cn 313 CS Building Department of Computer Science and Technology Nanjing University

Authentication Using Symmetric Keys Assumption -Without Trusted Third Party:each pair of parties share a secret key K -With Trusted Third Party:each party shares a secret key K with the 3rd party Threat model: -Message injection Inject a new message into a channel -Message modification Modify a message in a channel Message loss Delete a message in a channel -Message replay ●Replay an old message 2
2 Authentication Using Symmetric Keys Assumption ─ Without Trusted Third Party: each pair of parties share a secret key K ─ With Trusted Third Party: each party shares a secret key K with the 3rd party Threat model: ─ Message injection ● Inject a new message into a channel ─ Message modification ● Modify a message in a channel ─ Message loss ● Delete a message in a channel ─ Message replay ● Replay an old message

Without Trusted Third Party-Version 1 Alice Bob A,n,(nKAB Question:What is wrong with this authentication protocol? -Answer:vulnerable to replay attack. -How to fix this problem? 3
3 Without Trusted Third Party – Version 1 Question: What is wrong with this authentication protocol? ─ Answer: vulnerable to replay attack. ─ How to fix this problem? Alice Bob A, n, {n}KAB

Without Trusted Third Party-Version 2 Alice A Bob n (n KAB Question:What is wrong with this authentication protocol? -Answer:no session key is established,and no mutual authentication. -How to fix this problem?-Add session key kab and a nounce m from Alice 4
4 Without Trusted Third Party – Version 2 Question: What is wrong with this authentication protocol? ─ Answer: no session key is established, and no mutual authentication. ─ How to fix this problem? - Add session key kab, and a nounce m from Alice Alice A Bob n {n}KAB

Without Trusted Third Party-Final Version Alice A Bob n (n,Kab)KaB:m m kab Key management problems in authentication protocols without trusted third party: -1.Every pair of users need to have a shared secret key-too many keys. -2.Hard to manage:when a user joins a group,every one in the group needs to configure a new key with this person. -Solution:use a trusted third party-reduce n2 keys to n keys. 5
5 Without Trusted Third Party – Final Version Key management problems in authentication protocols without trusted third party: ─ 1. Every pair of users need to have a shared secret key – too many keys. ─ 2. Hard to manage: when a user joins a group, every one in the group needs to configure a new key with this person. ─ Solution: use a trusted third party – reduce n2 keys to n keys. Alice A Bob n {n, kab}KAB, m {m} kab
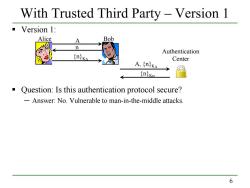
With Trusted Third Party-Version 1 Version 1: Alice A Bob n Authentication (n KA Center A,(nKA nKa Question:Is this authentication protocol secure? -Answer:No.Vulnerable to man-in-the-middle attacks. 6
6 With Trusted Third Party – Version 1 Version 1: Question: Is this authentication protocol secure? ─ Answer: No. Vulnerable to man-in-the-middle attacks. Alice A Bob n {n}KA A, {n}KA {n}KB Authentication Center
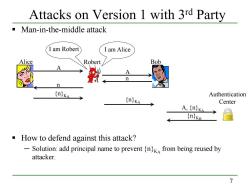
Attacks on Version 1 with 3rd Party Man-in-the-middle attack I am Robert I am Alice Alice Robert Bob A n Authentication Center A,(nika (nKB How to defend against this attack? -Solution:add principal name to prevent (n}k from being reused by attacker. 7
7 Man-in-the-middle attack How to defend against this attack? ─ Solution: add principal name to prevent {n}KA from being reused by attacker. Alice Bob A n {n}KA A, {n}KA {n}KB Authentication Center Robert A n {n}KA Attacks on Version 1 with 3rd Party I am Robert I am Alice
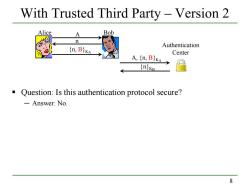
With Trusted Third Party -Version 2 Alice A Bob n Authentication (n,B)KA Center A,{n,BKA→ nKB Question:Is this authentication protocol secure? -Answer:No. 8
8 With Trusted Third Party – Version 2 Question: Is this authentication protocol secure? ─ Answer: No. Alice A Bob n {n, B}KA A, {n, B}KA {n}KB Authentication Center

Attacks on Version 2 with 3rd Party I am Alice Robert Bob A n Let me modify msg A,(n,B)KR Robert A,(n,B)KR Authentication R,(n,B)KR Center How to defend against this attack? -Solution:add principal name into nKB 9
9 Attacks on Version 2 with 3rd Party How to defend against this attack? ─ Solution: add principal name into {n}KB. Bob R, {n, B}KR {n}KB Authentication Center Robert A n A, {n, B}KR Robert A, {n, B}KR I am Alice Let me modify msg

With Trusted Third Party-Version 3 Alice A Bob n Authentication (n,B)KA Center A,{n,BKA→ Symmetry is not goodn A'KB Question:Is this authentication protocol secure? Answer:No. Hint:message symmetry in authentication protocols is not good. 10
10 With Trusted Third Party – Version 3 Question: Is this authentication protocol secure? ─ Answer: No. Hint: message symmetry in authentication protocols is not good. Alice A Bob n {n, B}KA A, {n, B}KA {n, A}KB Authentication Center Symmetry is not good
按次数下载不扣除下载券;
注册用户24小时内重复下载只扣除一次;
顺序:VIP每日次数-->可用次数-->下载券;
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)08 Authentication Using Asymmetric Keys.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)07 Hashes and Message Digests.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)06 Number Theory.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)05 Asymmetric Key Cryptography.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)04 Advanced Encryption Standard(AES).pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)03 Symmetric Key Cryptography.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)02 Security Principles.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)01 Introduction(戴海鹏).pdf
- 南京大学:《Java语言程序设计 Programming in Java》课程教学资源(教案讲义)Lecture 09 图形用户界面的设计与实现.ppt
- 南京大学:《Java语言程序设计 Programming in Java》课程教学资源(教案讲义)Lecture 08 数据结构与算法.ppt
- 南京大学:《Java语言程序设计 Programming in Java》课程教学资源(教案讲义)Lecture 07 Java 工具类.pdf
- 南京大学:《Java语言程序设计 Programming in Java》课程教学资源(教案讲义)Lecture 06 继承与多态.pdf
- 南京大学:《Java语言程序设计 Programming in Java》课程教学资源(教案讲义)Lecture 05 Java 类.ppt
- 南京大学:《Java语言程序设计 Programming in Java》课程教学资源(教案讲义)Lecture 05 Java 类.pdf
- 南京大学:《Java语言程序设计 Programming in Java》课程教学资源(教案讲义)Lecture 04 Java 语言基础.ppt
- 南京大学:《Java语言程序设计 Programming in Java》课程教学资源(教案讲义)Lecture 03 Java 编程入门.ppt
- 南京大学:《Java语言程序设计 Programming in Java》课程教学资源(教案讲义)Lecture 03 Java 编程入门.pdf
- 南京大学:《Java语言程序设计 Programming in Java》课程教学资源(教案讲义)Lecture 02 Java 概述.ppt
- 南京大学:《Java语言程序设计 Programming in Java》课程教学资源(教案讲义)Lecture 10 Java 高级编程.pdf
- 南京大学:《Java语言程序设计 Programming in Java》课程教学资源(教案讲义)Lecture 01 面向对象软件开发概述.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)10 Kerberos.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)11 Public-Key Infrastructure.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)12 Secure Socket Layer(SSL)、TLS(Transport Layer Security).pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)13 Human Authentication.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)14 Buffer Overflow Attacks.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)15 Bloom Filters and its Variants.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)16 Bloom Filter for Network Security.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)17 Web Security(Cookies and Cross Site Scripting,XSS).pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)18 Web Security(SQL Injection and Cross-Site Request Forgery).pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)19 Firewall Design Methods.pdf
- 《GPU并行编程 GPU Parallel Programming》课程教学资源(参考文献)MPI A Message-Passing Interface Standard(Version 2.2).pdf
- 《GPU并行编程 GPU Parallel Programming》课程教学资源(参考文献)An Asymmetric Distributed Shared Memory Model for Heterogeneous Parallel Systems.pdf
- 《GPU并行编程 GPU Parallel Programming》课程教学资源(参考文献)Software and the Concurrency Revolution.pdf
- 《GPU并行编程 GPU Parallel Programming》课程教学资源(参考文献)Some Computer Organizations and Their Effectiveness.pdf
- 《GPU并行编程 GPU Parallel Programming》课程教学资源(参考文献)Optimization Principles and Application Performance Evaluation of a Multithreaded GPU Using CUDA.pdf
- 《GPU并行编程 GPU Parallel Programming》课程教学资源(参考文献)Program Optimization Space Pruning for a Multithreaded GPU.pdf
- 《GPU并行编程 GPU Parallel Programming》课程教学资源(参考文献)Single-pass Parallel Prefix Scan with Decoupled Look-back.pdf
- 《GPU并行编程 GPU Parallel Programming》课程教学资源(参考文献)NVIDIA Parallel Prefix Sum(Scan)with CUDA(April 2007).pdf
- 《GPU并行编程 GPU Parallel Programming》课程教学资源(参考文献)Methods of conjugate gradients for solving linear systems.pdf
- 《GPU并行编程 GPU Parallel Programming》课程教学资源(参考文献)NVIDIA CUDA C Programming Guide(Design Guide,June 2017).pdf
