南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)14 Buffer Overflow Attacks

Buffer overflow attacks Haipeng Dai haipengdai@nju.edu.cn 313 CS Building Department of Computer Science and Technology Nanjing University
Buffer Overflow Attacks Haipeng Dai haipengdai@nju.edu.cn 313 CS Building Department of Computer Science and Technology Nanjing University

History:Morris Worm and Buffer Overflow Worm was released in 1988 by Robert Morris -Graduate student at Cornell.son of NSA chief scientist -Convicted under Computer Fraud and Abuse Act,sentenced to 3 years of probation and 400 hours of community service Now a computer science professor at MIT Worm was intended to propagate slowly and harmlessly measure the size of the Internet Due to a coding error,it created new copies as fast as it could and overloaded infected machines $10-100M worth of damage One of the worm's propagation techniques was a buffer overflow attack against a vulnerable version of fingerd on VAX systems By sending special string to finger daemon,worm caused it to execute code creating a new worm copy 一 Unable to determine remote OS version,worm also attacked fingerd on Suns running BSD,causing them to crash(instead of spawning a new copy) 2
2 History: Morris Worm and Buffer Overflow Worm was released in 1988 by Robert Morris ─ Graduate student at Cornell, son of NSA chief scientist ─ Convicted under Computer Fraud and Abuse Act, sentenced to 3 years of probation and 400 hours of community service ─ Now a computer science professor at MIT Worm was intended to propagate slowly and harmlessly measure the size of the Internet Due to a coding error, it created new copies as fast as it could and overloaded infected machines $10-100M worth of damage One of the worm’s propagation techniques was a buffer overflow attack against a vulnerable version of fingerd on VAX systems ─ By sending special string to finger daemon, worm caused it to execute code creating a new worm copy ─ Unable to determine remote OS version, worm also attacked fingerd on Suns running BSD, causing them to crash (instead of spawning a new copy)

Buffer Overflow These Days Most common cause of Internet attacks -Over 50%of advisories published by CERT(computer security incident report team)are caused by various buffer overflows Morris worm (1988):overflow in fingerd -6,000 machines infected CodeRed (2001):overflow in MS-IIS server -300,000 machines infected in 14 hours SQL Slammer (2003):overflow in MS-SQL server -75.000 machines infected in 10 minutes(!!) 3
3 Buffer Overflow These Days Most common cause of Internet attacks ─ Over 50% of advisories published by CERT (computer security incident report team) are caused by various buffer overflows Morris worm (1988): overflow in fingerd ─ 6,000 machines infected CodeRed (2001): overflow in MS-IIS server ─ 300,000 machines infected in 14 hours SQL Slammer (2003): overflow in MS-SQL server ─ 75,000 machines infected in 10 minutes (!!)
Attacks on Memory Buffers Buffer is a data storage area inside computer memory (stack or heap) -Intended to hold pre-defined amount of data If more data is stuffed into it,it spills into adjacent memory -If executable code is supplied as"data",victim's machine may be fooled into executing it-we'll see how .Code will self-propagate or give attacker control over machine First generation exploits:stack smashing Second gen:heaps,function pointers,off-by-one Third generation:format strings and heap management structures 4
4 Buffer is a data storage area inside computer memory (stack or heap) ─ Intended to hold pre-defined amount of data ● If more data is stuffed into it, it spills into adjacent memory ─ If executable code is supplied as “data”, victim’s machine may be fooled into executing it – we’ll see how ● Code will self-propagate or give attacker control over machine First generation exploits: stack smashing Second gen: heaps, function pointers, off-by-one Third generation: format strings and heap management structures Attacks on Memory Buffers
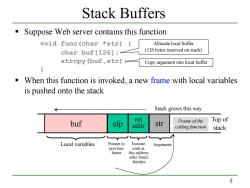
Stack Buffers Suppose Web server contains this function void func(char *str){ Allocate local buffer char buf[126]; (126 bytes reserved on stack) strcpy(buf,str) Copy argument into local buffer When this function is invoked,a new frame with local variables is pushed onto the stack Stack grows this way buf ret sfp rame of the。 Top of addr str calling function stack Local variables Pointer to Execute Arguments previous code at frame this address after func() finishes 5
5 Stack Buffers Suppose Web server contains this function void func(char *str) { char buf[126]; strcpy(buf,str); } When this function is invoked, a new frame with local variables is pushed onto the stack Allocate local buffer (126 bytes reserved on stack) Copy argument into local buffer Top of stack Stack grows this way buf sfp ret addr str Local variables Frame of the calling function Execute code at this address after func() finishes Pointer to Arguments previous frame

What If Buffer is Overstuffed? Memory pointed to by str is copied onto stack... void func(char *str){ char buf[126]; strcpy does NOT check whether the string strcpy(buf,str); at *str contains fewer than 126 characters a If a string longer than 126 bytes is copied into buffer,it will overwrite adjacent stack locations buf overflow str Frame of the Top of calling function stack This will be interpreted as return address! 6
6 What If Buffer is Overstuffed? Memory pointed to by str is copied onto stack… void func(char *str) { char buf[126]; strcpy(buf,str); } If a string longer than 126 bytes is copied into buffer, it will overwrite adjacent stack locations strcpy does NOT check whether the string at *str contains fewer than 126 characters buf str This will be interpreted as return address! overflow Top of stack Frame of the calling function
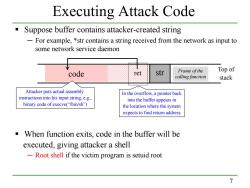
Executing Attack Code Suppose buffer contains attacker-created string For example,*str contains a string received from the network as input to some network service daemon str Frame of thie Top of code et ℃illing functto stack Attacker puts actual assembly In the overflow,a pointer back instructions into his input string,e.g., into the buffer appears in binary code of execve("/bin/sh") the location where the system expects to find return address When function exits,code in the buffer will be executed,giving attacker a shell -Root shell if the victim program is setuid root 7
7 Executing Attack Code Suppose buffer contains attacker-created string ─ For example, *str contains a string received from the network as input to some network service daemon When function exits, code in the buffer will be executed, giving attacker a shell ─ Root shell if the victim program is setuid root code str Frame of the calling function ret Attacker puts actual assembly instructions into his input string, e.g., binary code of execve(“/bin/sh”) In the overflow, a pointer back into the buffer appears in the location where the system expects to find return address Top of stack

Buffer Overflow Issues Executable attack code is stored on stack,inside the buffer containing attacker's string -Stack memory is supposed to contain only data,but... Overflow portion of the buffer must contain correct address of attack code in the RET position -The value in the RET position must point to the beginning of attack assembly code in the buffer Otherwise application will crash with segmentation violation -Attacker must correctly guess in which stack position his buffer will be when the function is called 8
8 Executable attack code is stored on stack, inside the buffer containing attacker’s string ─ Stack memory is supposed to contain only data, but… Overflow portion of the buffer must contain correct address of attack code in the RET position ─ The value in the RET position must point to the beginning of attack assembly code in the buffer ● Otherwise application will crash with segmentation violation ─ Attacker must correctly guess in which stack position his buffer will be when the function is called Buffer Overflow Issues

Problem:No Range Checking strcpy does not check input size strepy(buf,str)simply copies memory contents into buf starting from *str until10"is encountered,ignoring the size of area allocated to buf Many C library functions are unsafe -strcpy(char *dest,const char *src) -strcat(char *dest,const char *src) -gets(char *s) 一 scanf(const char *format,.. printf(const char *format,...) 9
9 Problem: No Range Checking strcpy does not check input size ─ strcpy(buf, str) simply copies memory contents into buf starting from *str until “\0” is encountered, ignoring the size of area allocated to buf Many C library functions are unsafe ─ strcpy(char *dest, const char *src) ─ strcat(char *dest, const char *src) ─ gets(char *s) ─ scanf(const char *format, …) ─ printf(const char *format, …)
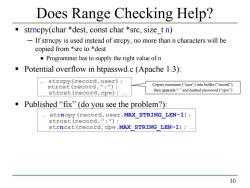
Does Range Checking Help? strncpy(char *dest,const char *src,size t n) -If strncpy is used instead of strcpy,no more than n characters will be copied from *src to *dest Programmer has to supply the right value ofn Potential overflow in htpasswd.c (Apache 1.3): strcpy(record,user); strcat (record,":"); Copies username("user")into buffer("record"), strcat (record,cpw)i then appends“.”and hashed password('cpw') Published“fix”(do you see the problem?): strncpy (record,user,MAX STRING LEN-1); strcat(record,":"); strncat (record,cpw,MAX STRING LEN-1);... 10
10 strncpy(char *dest, const char *src, size_t n) ─ If strncpy is used instead of strcpy, no more than n characters will be copied from *src to *dest ● Programmer has to supply the right value of n Potential overflow in htpasswd.c (Apache 1.3): … strcpy(record,user); strcat(record,”:”); strcat(record,cpw); … Published “fix” (do you see the problem?): … strncpy(record,user,MAX_STRING_LEN-1); strcat(record,”:”); strncat(record,cpw,MAX_STRING_LEN-1); … Does Range Checking Help? Copies username (“user”) into buffer (“record”), then appends “:” and hashed password (“cpw”)
按次数下载不扣除下载券;
注册用户24小时内重复下载只扣除一次;
顺序:VIP每日次数-->可用次数-->下载券;
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)13 Human Authentication.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)12 Secure Socket Layer(SSL)、TLS(Transport Layer Security).pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)11 Public-Key Infrastructure.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)10 Kerberos.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)09 Authentication Using Symmetric Keys.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)08 Authentication Using Asymmetric Keys.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)07 Hashes and Message Digests.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)06 Number Theory.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)05 Asymmetric Key Cryptography.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)04 Advanced Encryption Standard(AES).pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)03 Symmetric Key Cryptography.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)02 Security Principles.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)01 Introduction(戴海鹏).pdf
- 南京大学:《Java语言程序设计 Programming in Java》课程教学资源(教案讲义)Lecture 09 图形用户界面的设计与实现.ppt
- 南京大学:《Java语言程序设计 Programming in Java》课程教学资源(教案讲义)Lecture 08 数据结构与算法.ppt
- 南京大学:《Java语言程序设计 Programming in Java》课程教学资源(教案讲义)Lecture 07 Java 工具类.pdf
- 南京大学:《Java语言程序设计 Programming in Java》课程教学资源(教案讲义)Lecture 06 继承与多态.pdf
- 南京大学:《Java语言程序设计 Programming in Java》课程教学资源(教案讲义)Lecture 05 Java 类.ppt
- 南京大学:《Java语言程序设计 Programming in Java》课程教学资源(教案讲义)Lecture 05 Java 类.pdf
- 南京大学:《Java语言程序设计 Programming in Java》课程教学资源(教案讲义)Lecture 04 Java 语言基础.ppt
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)15 Bloom Filters and its Variants.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)16 Bloom Filter for Network Security.pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)17 Web Security(Cookies and Cross Site Scripting,XSS).pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)18 Web Security(SQL Injection and Cross-Site Request Forgery).pdf
- 南京大学:《网络安全与入侵检测 Network Security and Intrusion Detection》课程教学资源(课件讲稿)19 Firewall Design Methods.pdf
- 《GPU并行编程 GPU Parallel Programming》课程教学资源(参考文献)MPI A Message-Passing Interface Standard(Version 2.2).pdf
- 《GPU并行编程 GPU Parallel Programming》课程教学资源(参考文献)An Asymmetric Distributed Shared Memory Model for Heterogeneous Parallel Systems.pdf
- 《GPU并行编程 GPU Parallel Programming》课程教学资源(参考文献)Software and the Concurrency Revolution.pdf
- 《GPU并行编程 GPU Parallel Programming》课程教学资源(参考文献)Some Computer Organizations and Their Effectiveness.pdf
- 《GPU并行编程 GPU Parallel Programming》课程教学资源(参考文献)Optimization Principles and Application Performance Evaluation of a Multithreaded GPU Using CUDA.pdf
- 《GPU并行编程 GPU Parallel Programming》课程教学资源(参考文献)Program Optimization Space Pruning for a Multithreaded GPU.pdf
- 《GPU并行编程 GPU Parallel Programming》课程教学资源(参考文献)Single-pass Parallel Prefix Scan with Decoupled Look-back.pdf
- 《GPU并行编程 GPU Parallel Programming》课程教学资源(参考文献)NVIDIA Parallel Prefix Sum(Scan)with CUDA(April 2007).pdf
- 《GPU并行编程 GPU Parallel Programming》课程教学资源(参考文献)Methods of conjugate gradients for solving linear systems.pdf
- 《GPU并行编程 GPU Parallel Programming》课程教学资源(参考文献)NVIDIA CUDA C Programming Guide(Design Guide,June 2017).pdf
- 电子科技大学:《GPU并行编程 GPU Parallel Programming》课程教学资源(课件讲稿)Lecture 01 Introduction To Cuda C.pdf
- 电子科技大学:《GPU并行编程 GPU Parallel Programming》课程教学资源(课件讲稿)Lecture 02 CUDA PARALLELISM MODEL.pdf
- 电子科技大学:《GPU并行编程 GPU Parallel Programming》课程教学资源(课件讲稿)Lecture 03 MEMORY AND DATA LOCALITY.pdf
- 电子科技大学:《GPU并行编程 GPU Parallel Programming》课程教学资源(课件讲稿)Lecture 04 Performance considerations.pdf
- 电子科技大学:《GPU并行编程 GPU Parallel Programming》课程教学资源(课件讲稿)Lecture 05 PARALLEL COMPUTATION PATTERNS(HISTOGRAM).pdf
