电子科技大学:《大数据分析与挖掘 Big Data Analysis and Mining》课程教学资源(课件讲稿)Lecture 6 Graph Mining

Lecture 6 Graph Mining
Lecture 6 Graph Mining

Background Graph Mining Networks/Graphs--exist everywhere. Food Web of Smallmouth Bass Leech Little Rock Lake (Cannibal) 1st Tropic Level Mosty Phytoplankton 2nd Trophic Level Many Zooplankton Internet Food Web The Social Stcture of Coutryside"Schod District T和出Ody2 Friendship Network Co-author networks
Internet Food Web Friendship Network Co-author networks Networks/Graphs -- exist everywhere. Background Graph Mining

Background Graph Mining Origin of Graph Theory: Seven Bridges of Konigsberg(proposed by Leonhard Euler()) --wiki The city of Konigsberg in Prussia(now Kaliningrad,Russia)was set on both sides of the Pregel River,and included two large islands which were connected to each other,or to the two mainland portions of the city,by seven bridges.The problem was to devise a walk through the city that would cross each of those bridges once and only once
Origin of Graph Theory: Seven Bridges of Königsberg (proposed by Leonhard Euler(欧拉)) The city of Königsberg in Prussia (now Kaliningrad, Russia) was set on both sides of the Pregel River, and included two large islands which were connected to each other, or to the two mainland portions of the city, by seven bridges. The problem was to devise a walk through the city that would cross each of those bridges once and only once. --wiki Background Graph Mining
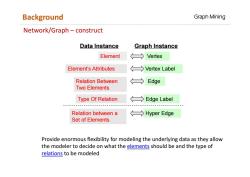
Background Graph Mining Network/Graph-construct Data Instance Graph Instance Element Vertex Element's Attributes >Vertex Label Relation Between Edge Two Elements Type Of Relation Edge Label Relation between a →Hyper Edge Set of Elements Provide enormous flexibility for modeling the underlying data as they allow the modeler to decide on what the elements should be and the type of relations to be modeled
Network/Graph – construct Element Vertex Element’s Attributes Relation Between Two Elements Type Of Relation Vertex Label Edge Label Edge Data Instance Graph Instance Relation between a Set of Elements Hyper Edge Provide enormous flexibility for modeling the underlying data as they allow the modeler to decide on what the elements should be and the type of relations to be modeled Background Graph Mining

Background Graph Mining Networks/Graphs-applications in real-world? Information Maximization ·viral'marketing. Web-log ('blog')news propagation. Computer network security Email/IP traffic and anomaly detection ·Prediction The prediction of flow within networks
Networks/Graphs – applications in real-world? • Information Maximization • ‘viral’ marketing. • Web-log (‘blog’) news propagation. • Computer network security • Email/IP traffic and anomaly detection • Prediction • The prediction of flow within networks Background Graph Mining
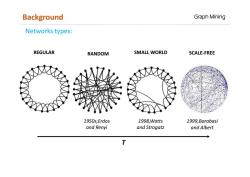
Background Graph Mining Networks types: REGULAR RANDOM SMALL WORLD SCALE-FREE 1950s,Erdos 1998,Watts 1999,Barabasi and Renyi and Strogatz and Albert T
Networks types: REGULAR SMALL WORLD RANDOM SCALE-FREE T 1950s,Erdos and Renyi 1998,Watts and Strogatz 1999,Barabasi and Albert Background Graph Mining

Background Graph Mining Small world network: Six degree of separation The average distance between two randomly individuals in the USA:6 The average distance between two 10234④5⑤6( randomly users in Facebook(721 million active users,69 billion links )4.74
Small world network: Six degree of separation ¾ The average distance between two randomly individuals in the USA : 6 ¾ The average distance between two randomly users in Facebook(721 million active users, 69 billion links ) : 4.74 ¾ … Background Graph Mining
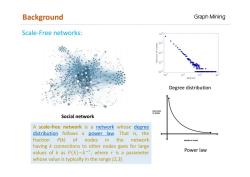
Background Graph Mining Scale-Free networks: 100 10 10 10 10 10 10 degree Degree distribution 62 Social network A scale-free network is a network whose degree distribution follows a power law. That i is,the fraction P的 of nodes in the network DEBREE OF NODES having k connections to other nodes goes for large values of k as P(k)~kT,where r is a parameter Power law whose value is typically in the range(2,3)
Scale-Free networks: A scale-free network is a network whose degree distribution follows a power law. That is, the fraction P(k) of nodes in the network having k connections to other nodes goes for large values of k as ି, where is a parameter whose value is typically in the range (2,3). Social network Degree distribution Power law Background Graph Mining

Key Node ldentification
Key Node Identification

Key Node ldentification Graph Mining >How should we select some special customers to viral market efficiently if we have a limited budget? >Which countries have a huge impact on the global trade? >Who hold great power on the terrorist organization? >Which node is the weakest position in the power supply network? 丝绸之路 微哈拉沙流 4m千 来品 八千方勿之
¾ How should we select some special customers to viral market efficiently if we have a limited budget? ¾ Which countries have a huge impact on the global trade? ¾ Who hold great power on the terrorist organization? ¾ Which node is the weakest position in the power supply network? Background Key Node Identification Graph Mining
按次数下载不扣除下载券;
注册用户24小时内重复下载只扣除一次;
顺序:VIP每日次数-->可用次数-->下载券;
- 电子科技大学:《大数据分析与挖掘 Big Data Analysis and Mining》课程教学资源(课件讲稿)Lecture 5 Data Stream Mining.pdf
- 电子科技大学:《大数据分析与挖掘 Big Data Analysis and Mining》课程教学资源(课件讲稿)Lecture 4 Sampling for Big Data.pdf
- 电子科技大学:《大数据分析与挖掘 Big Data Analysis and Mining》课程教学资源(课件讲稿)Lecture 3 Hashing.pdf
- 电子科技大学:《大数据分析与挖掘 Big Data Analysis and Mining》课程教学资源(课件讲稿)Lecture 2 BasicConcepts(Foundations of Data Mining).pdf
- 电子科技大学:《大数据分析与挖掘 Big Data Analysis and Mining》课程教学资源(课件讲稿)Lecture 1 Intro(主讲:邵俊明).pdf
- 计算机科学与技术(PPT讲稿)Unlock with Your Heart - Heartbeat-based Authentication on Commercial Mobile Phones.pptx
- 计算机科学与技术(参考文献)VECTOR - Velocity Based Temperature-field Monitoring with Distributed Acoustic Devices.pdf
- 计算机科学与技术(参考文献)VSkin - Sensing Touch Gestures on Surfaces of Mobile Devices Using Acoustic Signals.pdf
- 计算机科学与技术(参考文献)RespTracker - Multi-user Room-scale Respiration Tracking with Commercial Acoustic Devices.pdf
- 计算机科学与技术(参考文献)Dynamic Speed Warping - Similarity-Based One-shot Learning for Device-free Gesture Signals.pdf
- 计算机科学与技术(参考文献)SpiderMon - Towards Using Cell Towers as Illuminating Sources for Keystroke Monitoring.pdf
- 计算机科学与技术(参考文献)Unlock with Your Heart:Heartbeat-based Authentication on Commercial Mobile Phones.pdf
- 计算机科学与技术(参考文献)QGesture - Quantifying Gesture Distance and Direction with WiFi Signals.pdf
- 计算机科学与技术(PPT讲稿)QGesture - Quantifying Gesture Distance and Direction with WiFi Signals.pptx
- 计算机科学与技术(参考文献)Gait Recognition Using WiFi Signals.pdf
- 计算机科学与技术(参考文献)Gait Recognition Using WiFi Signals.pdf
- 计算机科学与技术(参考文献)Depth Aware Finger Tapping on Virtual Displays.pdf
- 计算机科学与技术(参考文献)Device-Free Gesture Tracking Using Acoustic Signals.pdf
- 计算机科学与技术(参考文献)Device-Free Gesture Tracking Using Acoustic Signals.pdf
- 计算机科学与技术(参考文献)Depth Aware Finger Tapping on Virtual Display.pdf
- 电子科技大学:《大数据分析与挖掘 Big Data Analysis and Mining》课程教学资源(课件讲稿)Lecture 7 Hadoop-Spark.pdf
- 电子科技大学:《先进计算机网络技术》课程教学资源(课件讲稿)Introduction(冯钢).pdf
- 电子科技大学:《先进计算机网络技术》课程教学资源(课件讲稿)Unit 1 Overview - A big Picture on Traffic Control and QoS in IP networks.pdf
- 电子科技大学:《先进计算机网络技术》课程教学资源(课件讲稿)Unit 2 Call-level Models and Admission Control.pdf
- 电子科技大学:《先进计算机网络技术》课程教学资源(课件讲稿)Unit 3 Traffic Policing and Shaping.pdf
- 电子科技大学:《先进计算机网络技术》课程教学资源(课件讲稿)Unit 4 TCP Traffic Control.pdf
- 电子科技大学:《先进计算机网络技术》课程教学资源(课件讲稿)Unit 5 Buffer Management.pdf
- 电子科技大学:《先进计算机网络技术》课程教学资源(课件讲稿)Unit 6 Packet Scheduling.pdf
- 电子科技大学:《先进计算机网络技术》课程教学资源(课件讲稿)Unit 7 IntServ/RSVP and DiffServ.pdf
- 电子科技大学:《先进计算机网络技术》课程教学资源(课件讲稿)Unit 8 Traffic Management and Modeling.pdf
- 电子科技大学:《先进计算机网络技术》课程教学资源(课件讲稿)Unit 9 Network Traffic Engineering.pdf
- 电子科技大学:《先进计算机网络技术》课程教学资源(课件讲稿)Unit 10 Network Coding and Traffic Balancing.pdf
- 电子科技大学:《先进计算机网络技术》课程教学资源(课件讲稿)Unit 11 AI Enabled Wireless Access Control and Handoff.pdf
- 《机器学习 Machine Learning》课程教学资源(实践资料)华为Atlas人工智能计算解决方案产品彩页.pdf
- 《机器学习 Machine Learning》课程教学资源(实践资料)Xshell远程登陆开发板方法(华为atlas800 - 910).pdf
- 《机器学习 Machine Learning》课程教学资源(实践资料)MNIST手写体识别实验.pdf
- 《机器学习 Machine Learning》课程教学资源(实践资料)MNIST手写数字识别的Atlas 200DK推理应用.pdf
- 《机器学习 Machine Learning》课程教学资源(实践资料)ModelArts花卉识别(基于MindSpore的图像识别全流程代码实战).pdf
- 《机器学习 Machine Learning》课程教学资源(书籍文献)[德] Andreas C. Müller [美] Sarah Guido《Python机器学习基础教程 Introduction to Machine Learning with Python》.pdf
- 《机器学习 Machine Learning》课程教学资源(书籍文献)[美] 弗朗索瓦·肖莱《Python深度学习 Deep Learning with Python》.pdf
