电子科技大学:《先进计算机网络技术》课程教学资源(课件讲稿)Unit 3 Traffic Policing and Shaping

Feng Gang National Laboratory of Communication,UESTC Aug 2017 Ver 1.4 Unit 3 Traffic Policing and Shaping 2616009:Network Traffic Engineering 3:Traffic Policing and Shaping Page.1
2616009: Network Traffic Engineering Feng Gang National Laboratory of Communication, UESTC Aug 2017 Ver 1.4 3: Traffic Policing and Shaping Page.1 Unit 3 Traffic Policing and Shaping

Feng Gang National Laboratory of Communication,UESTC Aug 2017 Ver 1.4 Roadmap Traffic Shaping and Policing -What and why is traffic shaping and traffic policing Leaky Bucket Token Bucket Traffic -Generic Cell Rate Algorithm (GCRA) -Virtual scheduling algorithm implementati Leaky bucket algorithm implementation 2616009:Network Traffic Engineering 3:Traffic Policing and Shaping Page.2
2616009: Network Traffic Engineering Feng Gang National Laboratory of Communication, UESTC Aug 2017 Ver 1.4 3: Traffic Policing and Shaping Page.2 Roadmap • Traffic Shaping and Policing What and why is traffic shaping and traffic policing Leaky Bucket Token Bucket Traffic Generic Cell Rate Algorithm (GCRA) -Virtual scheduling algorithm implementati - Leaky bucket algorithm implementation

Feng Gang National Laboratory of Communication,UESTC Aug 2017 Ver 1.4 Traffic Policing Question: A connection accepted by CAC,it's QoS can be satisfied,if the source obeys the traffic descriptor.What happens if the traffic flow violates the initial contract? Answer: The network may not maintain acceptable performance What can be done? Traffic Policing is performed by the network to ensure that the parameter specified by the user are being complied. Traffic Policing The process of monitoring and enforcing the traffic flow What Traffic Policing do? Discard the nonconforming traffic S Tag the nonconforming traffic with lower priority) 2616009:Network Traffic Engineering 3:Traffic Policing and Shaping Page.3
2616009: Network Traffic Engineering Feng Gang National Laboratory of Communication, UESTC Aug 2017 Ver 1.4 3: Traffic Policing and Shaping Page.3 Traffic Policing • Question: A connection accepted by CAC, it’s QoS can be satisfied, if the source obeys the traffic descriptor. What happens if the traffic flow violates the initial contract? • Answer: The network may not maintain acceptable performance • What can be done? Traffic Policing is performed by the network to ensure that the parameter specified by the user are being complied. • Traffic Policing The process of monitoring and enforcing the traffic flow • What Traffic Policing do? §Discard the nonconforming traffic §Tag the nonconforming traffic ( with lower priority)

Feng Gang National Laboratory of Communication,UESTC Aug 2017 Ver 1.4 Leaky Bucket Faucet packet unregulated flow Leaky bucket Host Compute (Overflow = Non-Conforming Traffic) The bucket holds packets Water Water drips out at a Interface containing a constant rate 0 leaky bucket 0 0(Conforming Traffic) 回 0 Regulated flow 口 Network Provides traffic shaping:Input bursty.Output rate controlled. Provides traffic policing:Ensure that users are sending traffic within specified limits Excess traffic discarded or admitted with CLP=1 2616009:Network Traffic Engineering 3:Traffic Policing and Shaping Page.4
2616009: Network Traffic Engineering Feng Gang National Laboratory of Communication, UESTC Aug 2017 Ver 1.4 3: Traffic Policing and Shaping Page.4 Leaky Bucket Faucet Leaky bucket Water drips out at a constant rate (Overflow => Non-Conforming Traffic) ( Conforming Traffic ) Water unregulated flow Host Computer Network packet The bucket holds packets Regulated flow Interface containing a leaky bucket • Provides traffic shaping: Input bursty. Output rate controlled. • Provides traffic policing: Ensure that users are sending traffic within specified limits Excess traffic discarded or admitted with CLP = 1
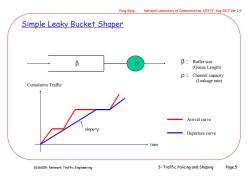
Feng Gang National Laboratory of Communication,UESTC Aug 2017 Ver 1.4 Simple Leaky Bucket Shaper B β: Buffer size (Queue Length) p:Channel capacity (Leakage rate) Cumulative Traffic Arrival curve slope=p Departure curve time 2616009:Network Traffic Engineering 3:Traffic Policing and Shaping Page.5
2616009: Network Traffic Engineering Feng Gang National Laboratory of Communication, UESTC Aug 2017 Ver 1.4 3: Traffic Policing and Shaping Page.5 Simple Leaky Bucket Shaper b Cumulative Traffic slope= time Arrival curve Departure curve b: : Buffer size (Queue Length) Channel capacity (Leakage rate)
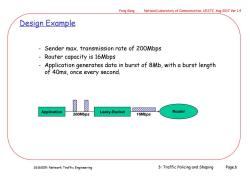
Feng Gang National Laboratory of Communication,UESTC Aug 2017 Ver 1.4 Design Example Sender max.transmission rate of 200Mbps Router capacity is 16Mbps Application generates data in burst of 8Mb,with a burst length of 40ms,once every second. ☑ Application Router 200Mbps Leaky-Bucket 16Mbps 2616009:Network Traffic Engineering 3:Traffic Policing and Shaping Page.6
2616009: Network Traffic Engineering Feng Gang National Laboratory of Communication, UESTC Aug 2017 Ver 1.4 3: Traffic Policing and Shaping Page.6 - Sender max. transmission rate of 200Mbps - Router capacity is 16Mbps - Application generates data in burst of 8Mb, with a burst length of 40ms, once every second. Application Leaky-Bucket Router 200Mbps 16Mbps Design Example

Feng Gang National Laboratory of Communication,UESTC Aug 2017 Ver 1.4 Design Example First make sure the router can possibly handle the traffic: Average data rate generated by application is: Total 8Mb/1s 8Mbps router's capacity (16Mbps) Then determines Cfor the leaky bucket: 200Mbps →16Mbps Let A be arrival rate,and Tbe burst length (in seconds),then C>max{(total received in time f)-(total tx in time )Vf =A*t-*t=(A-0t =(200-16)*0.04 =7.36Mbor0.92MB 2616009:Network Traffic Engineering 3:Traffic Policing and Shaping Page.7
2616009: Network Traffic Engineering Feng Gang National Laboratory of Communication, UESTC Aug 2017 Ver 1.4 3: Traffic Policing and Shaping Page.7 Design Example • First make sure the router can possibly handle the traffic: • Then determines C for the leaky bucket: Average data rate generated by application is: Total = 8Mb/1s = 8Mbps < router’s capacity (16Mbps) 200Mbps 16Mbps C Let A be arrival rate, and T be burst length (in seconds), then C max{(total received in time t)-(total tx in time t)|"t} = A*t - r*t = (A-r)t = (200-16)*0.04 = 7.36Mb or 0.92MB

Feng Gang National Laboratory of Communication,UESTC Aug 2017 Ver 1.4 The Leaky Bucket Algorithm-Design example (cont'd) 目 25M日/sec for40msec (a】 Tim e (m sec)- 500 (b) 2M日sec for500msec Tim e (m sec) 500 (a)Input to a leaky bucket (b)Output from a leaky bucket 2616009:Network Traffic Engineering 3:Traffic Policing and Shaping Page.8
2616009: Network Traffic Engineering Feng Gang National Laboratory of Communication, UESTC Aug 2017 Ver 1.4 3: Traffic Policing and Shaping Page.8 The Leaky Bucket Algorithm—Design example (cont’d) (a) Input to a leaky bucket (b) Output from a leaky bucket

Feng Gang National Laboratory of Communication,UESTC Aug 2017 Ver 1.4 Token Bucket Traffic Shaper Why a token bucket traffic shaper? S Leaky bucket:the output rate is constant when the buffer is not empty: only CBR is allowed. Token Bucket Shaper (Dual-bucket Shaper) §2 buckets One buffer for data One buffer for a pool of tokens:tokens are generated at a constant rate S More flexible:allows for some burstiness in the traffic as long as it is under a certain limit Conforming packets are passed through without further delay 2616009:Network Traffic Engineering 3:Traffic Policing and Shaping Page.9
2616009: Network Traffic Engineering Feng Gang National Laboratory of Communication, UESTC Aug 2017 Ver 1.4 3: Traffic Policing and Shaping Page.9 Token Bucket Traffic Shaper • Why a token bucket traffic shaper? §Leaky bucket: the output rate is constant when the buffer is not empty: only CBR is allowed. • Token Bucket Shaper (Dual-bucket Shaper) §2 buckets – One buffer for data – One buffer for a pool of tokens: tokens are generated at a constant rate §More flexible: allows for some burstiness in the traffic as long as it is under a certain limit §Conforming packets are passed through without further delay
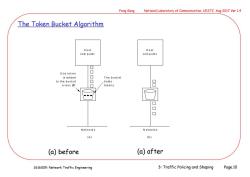
Feng Gang National Laboratory of Communication,UESTC Aug 2017 Ver 1.4 The Token Bucket Algorithm Host Host com puter com puter One token is added The bucket to the buck et holds every△T tokens Networks Networks (a) (b) (a)before (a)after 2616009:Network Traffic Engineering 3:Traffic Policing and Shaping Page.10
2616009: Network Traffic Engineering Feng Gang National Laboratory of Communication, UESTC Aug 2017 Ver 1.4 3: Traffic Policing and Shaping Page.10 The Token Bucket Algorithm (a) before (a) after
按次数下载不扣除下载券;
注册用户24小时内重复下载只扣除一次;
顺序:VIP每日次数-->可用次数-->下载券;
- 电子科技大学:《先进计算机网络技术》课程教学资源(课件讲稿)Unit 2 Call-level Models and Admission Control.pdf
- 电子科技大学:《先进计算机网络技术》课程教学资源(课件讲稿)Unit 1 Overview - A big Picture on Traffic Control and QoS in IP networks.pdf
- 电子科技大学:《先进计算机网络技术》课程教学资源(课件讲稿)Introduction(冯钢).pdf
- 电子科技大学:《大数据分析与挖掘 Big Data Analysis and Mining》课程教学资源(课件讲稿)Lecture 7 Hadoop-Spark.pdf
- 电子科技大学:《大数据分析与挖掘 Big Data Analysis and Mining》课程教学资源(课件讲稿)Lecture 6 Graph Mining.pdf
- 电子科技大学:《大数据分析与挖掘 Big Data Analysis and Mining》课程教学资源(课件讲稿)Lecture 5 Data Stream Mining.pdf
- 电子科技大学:《大数据分析与挖掘 Big Data Analysis and Mining》课程教学资源(课件讲稿)Lecture 4 Sampling for Big Data.pdf
- 电子科技大学:《大数据分析与挖掘 Big Data Analysis and Mining》课程教学资源(课件讲稿)Lecture 3 Hashing.pdf
- 电子科技大学:《大数据分析与挖掘 Big Data Analysis and Mining》课程教学资源(课件讲稿)Lecture 2 BasicConcepts(Foundations of Data Mining).pdf
- 电子科技大学:《大数据分析与挖掘 Big Data Analysis and Mining》课程教学资源(课件讲稿)Lecture 1 Intro(主讲:邵俊明).pdf
- 计算机科学与技术(PPT讲稿)Unlock with Your Heart - Heartbeat-based Authentication on Commercial Mobile Phones.pptx
- 计算机科学与技术(参考文献)VECTOR - Velocity Based Temperature-field Monitoring with Distributed Acoustic Devices.pdf
- 计算机科学与技术(参考文献)VSkin - Sensing Touch Gestures on Surfaces of Mobile Devices Using Acoustic Signals.pdf
- 计算机科学与技术(参考文献)RespTracker - Multi-user Room-scale Respiration Tracking with Commercial Acoustic Devices.pdf
- 计算机科学与技术(参考文献)Dynamic Speed Warping - Similarity-Based One-shot Learning for Device-free Gesture Signals.pdf
- 计算机科学与技术(参考文献)SpiderMon - Towards Using Cell Towers as Illuminating Sources for Keystroke Monitoring.pdf
- 计算机科学与技术(参考文献)Unlock with Your Heart:Heartbeat-based Authentication on Commercial Mobile Phones.pdf
- 计算机科学与技术(参考文献)QGesture - Quantifying Gesture Distance and Direction with WiFi Signals.pdf
- 计算机科学与技术(PPT讲稿)QGesture - Quantifying Gesture Distance and Direction with WiFi Signals.pptx
- 计算机科学与技术(参考文献)Gait Recognition Using WiFi Signals.pdf
- 电子科技大学:《先进计算机网络技术》课程教学资源(课件讲稿)Unit 4 TCP Traffic Control.pdf
- 电子科技大学:《先进计算机网络技术》课程教学资源(课件讲稿)Unit 5 Buffer Management.pdf
- 电子科技大学:《先进计算机网络技术》课程教学资源(课件讲稿)Unit 6 Packet Scheduling.pdf
- 电子科技大学:《先进计算机网络技术》课程教学资源(课件讲稿)Unit 7 IntServ/RSVP and DiffServ.pdf
- 电子科技大学:《先进计算机网络技术》课程教学资源(课件讲稿)Unit 8 Traffic Management and Modeling.pdf
- 电子科技大学:《先进计算机网络技术》课程教学资源(课件讲稿)Unit 9 Network Traffic Engineering.pdf
- 电子科技大学:《先进计算机网络技术》课程教学资源(课件讲稿)Unit 10 Network Coding and Traffic Balancing.pdf
- 电子科技大学:《先进计算机网络技术》课程教学资源(课件讲稿)Unit 11 AI Enabled Wireless Access Control and Handoff.pdf
- 《机器学习 Machine Learning》课程教学资源(实践资料)华为Atlas人工智能计算解决方案产品彩页.pdf
- 《机器学习 Machine Learning》课程教学资源(实践资料)Xshell远程登陆开发板方法(华为atlas800 - 910).pdf
- 《机器学习 Machine Learning》课程教学资源(实践资料)MNIST手写体识别实验.pdf
- 《机器学习 Machine Learning》课程教学资源(实践资料)MNIST手写数字识别的Atlas 200DK推理应用.pdf
- 《机器学习 Machine Learning》课程教学资源(实践资料)ModelArts花卉识别(基于MindSpore的图像识别全流程代码实战).pdf
- 《机器学习 Machine Learning》课程教学资源(书籍文献)[德] Andreas C. Müller [美] Sarah Guido《Python机器学习基础教程 Introduction to Machine Learning with Python》.pdf
- 《机器学习 Machine Learning》课程教学资源(书籍文献)[美] 弗朗索瓦·肖莱《Python深度学习 Deep Learning with Python》.pdf
- 《机器学习 Machine Learning》课程教学资源(书籍文献)Finding Structure in Time.pdf
- 《机器学习 Machine Learning》课程教学资源(书籍文献)Learning representations by back-propagating errors.pdf
- 《机器学习 Machine Learning》课程教学资源(书籍文献)Attention Is All You Need.pdf
- 《机器学习 Machine Learning》课程教学资源(书籍文献)Gradient-Based Learning Applied to Document Recognition.pdf
- 《机器学习 Machine Learning》课程教学资源(书籍文献)Handwritten Digit Recognition with a Back-Propagation Network.pdf
