信息安全专业教学资源(讲稿)Artificial Immune Systems——An Emerging Technology

Artificial Immune Systems:An Emerging Technology Congress on Evolutionary Computation 2001. Seoul,Korea. Dr.Jonathan Timmis Computing Laboratory University of Kent at Canterbury England.UK J.Timmis@ukc.ac.uk http:/www.cs.ukc.ac.uk/people/staff/jt6
Artificial Immune Systems: An Emerging Technology Dr. Jonathan Timmis Computing Laboratory University of Kent at Canterbury England. UK. J.Timmis@ukc.ac.uk http:/www.cs.ukc.ac.uk/people/staff/jt6 Congress on Evolutionary Computation 2001. Seoul, Korea

Tutorial Overview 一--一一--一一-0-一一-0-一一--一一- 一一--一一--一一--一一- What are Artificial Immune Systems? Background immunology .Why use the immune system as a metaphor *Immune Metaphors employed 张Review of AIS work ◆Applications More blue sky research CEC 2001 Artificial Immune Systems
CEC 2001 Artificial Immune Systems Tutorial Overview What are Artificial Immune Systems? Background immunology Why use the immune system as a metaphor Immune Metaphors employed Review of AIS work Applications More blue sky research
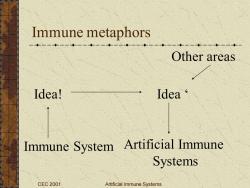
Immune metaphors --一一--一一-- Other areas Idea! Idea Immune System Artificial Immune Systems CEC 2001 Artificial Immune Systems
CEC 2001 Artificial Immune Systems Immune metaphors Immune System Idea! Idea ‘ Other areas Artificial Immune Systems

Artificial Immune Systems -一一--一一--一一--一一-0 Relatively new branch of computer science ◆Some history Using natural immune system as a metaphor for solving computational problems .Not modelling the immune system Variety of applications so far .Fault diagnosis (Ishida) Computer security (Forrest,Kim) .Novelty detection(Dasgupta) Robot behaviour (Lee) .Machine learning(Hunt,Timmis,de Castro) CEC 2001 Artificial Immune Systems
CEC 2001 Artificial Immune Systems Artificial Immune Systems Relatively new branch of computer science Some history Using natural immune system as a metaphor for solving computational problems Not modelling the immune system Variety of applications so far … Fault diagnosis (Ishida) Computer security (Forrest, Kim) Novelty detection (Dasgupta) Robot behaviour (Lee) Machine learning (Hunt, Timmis, de Castro)

Why the Immune System? 装Recognition ◆Anomaly detection ◆Noise tolerance 米Robustness 袋Feature extraction 米 Diversity Reinforcement learning 米Memory 米Distributed 米Multi-layered 张Adaptive CEC 2001 Artificial Immune Systems
CEC 2001 Artificial Immune Systems Why the Immune System? Recognition Anomaly detection Noise tolerance Robustness Feature extraction Diversity Reinforcement learning Memory Distributed Multi-layered Adaptive

一一--一一- Part I-Basic Immunology CEC 2001 Artificial Immune Systems
CEC 2001 Artificial Immune Systems Part I – Basic Immunology

Role of the Immune System ---一--一一--一一--一一--一一--一一---一- Protect our bodies from infection Primary immune response .Launch a response to invading pathogens Secondary immune response Remember past encounters Faster response the second time around CEC 2001 Artificial Immune Systems
CEC 2001 Artificial Immune Systems Role of the Immune System Protect our bodies from infection Primary immune response Launch a response to invading pathogens Secondary immune response Remember past encounters Faster response the second time around
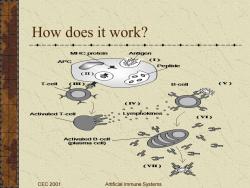
How does it work? --0-一一--一一--一一-0-一一--一一--一一--一一--一一- -一一--一一--一一-- MHC protein Antigen APC (亚) Peptide ()( 感 T-cell B-cell 〔v) Activated T-cell 。Lymphokines Activated B-cell (plasma cell) 3 (v) CEC 2001 Artificial Immune Systems
CEC 2001 Artificial Immune Systems How does it work?
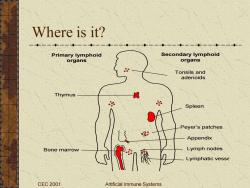
Where is it? --一一--一一-0-一一--一 -一---一--一一-0-一--一一--- Primary lymphoid Secondary lymphoid organs organs Tonsils and adenoids Thymus H 必 Spleen Peyer's patches Appendix Bone marrow Lymph nodes Lymphatic vesse CEC 2001 Artificial Immune Systems
CEC 2001 Artificial Immune Systems Where is it? Lymphatic vessels Lymph nodes Thymus Spleen Tonsils and adenoids Bone marrow Appendix Peyer’s patches Primary lymphoid organs Secondary lymphoid organs
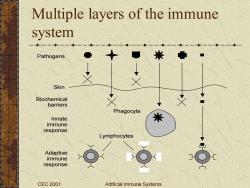
Multiple layers of the immune system Pathogens ↓ Skin Biochemical barriers Phagocyte Innate immune response Lymphocytes Adaptive immune response CEC 2001 Artificial Immune Systems
CEC 2001 Artificial Immune Systems Multiple layers of the immune system Phagocyte Adaptive immune response Lymphocytes Innate immune response Biochemical barriers Skin Pathogens
按次数下载不扣除下载券;
注册用户24小时内重复下载只扣除一次;
顺序:VIP每日次数-->可用次数-->下载券;
- 安徽理工大学:信息安全专业教学资源(讲稿)Bot、Botnet及其检测技术.pdf
- 安徽理工大学:信息安全专业教学资源(讲稿)Advance in Intrusion Detection Techniques.ppt
- 信息安全专业参考书籍:《Mathematics for Computer Science》计算机科学数学(revised Monday 5th June, 2017,Eric Lehman、F Thomson Leighton、Albert R Meyer).pdf
- 安徽理工大学:信息安全专业教学资源(讲稿)学科前沿讲座之一.pptx
- 安徽理工大学:《Linux开发基础 Development Foundation on Linux OS》课程教学资源(PPT课件讲稿)Section 4 Perl编程(附Perl源代码).ppt
- 安徽理工大学:《Linux开发基础 Development Foundation on Linux OS》课程教学资源(PPT课件讲稿)Section 4 Perl programming.ppt
- 清华大学出版社:《GNU/Linux编程指南》参考书籍【美】K. Wall,M. Watson, M. Whitis(共39章).pdf
- 安徽理工大学:《Linux开发基础 Development Foundation on Linux OS》课程教学资源(PPT课件讲稿)Section 2、3 GNU C/C++编程(CGI programming in GNU C/C++ language).ppt
- 安徽理工大学:《Linux开发基础 Development Foundation on Linux OS》课程教学资源(PPT课件讲稿)Section 1 Shell编程 Shell programming on Linux OS.ppt
- 清华大学出版社:《智能技术》课程教学资源(PPT课件讲稿)第8章 机器学习 machine learning.ppt
- 清华大学出版社:《智能技术》课程教学资源(PPT课件讲稿)第4章 模糊逻辑技术 fuzzy logic(编著:曹承志).ppt
- 清华大学出版社:《智能技术》课程教学资源(PPT课件讲稿)第6章 遗传算法(genetic algorithms,GA).ppt
- 安徽理工大学:《计算机安全与密码学 Computer Security and Cryptography》课程教学资源(课件讲稿)密钥管技术理 Key Management.pdf
- 哈尔滨工程大学:《计算机安全与密码学 Computer Security and Cryptography》课程教学资源(课件讲稿)数字签名技术 Digital Signature.pdf
- 哈尔滨工程大学:《计算机安全与密码学 Computer Security and Cryptography》课程教学资源(课件讲稿)公钥密码体制 Public Key Cryptography.pdf
- 哈尔滨工程大学:《计算机安全与密码学 Computer Security and Cryptography》课程教学资源(课件讲稿)散列函数与消息认证码 Hash and Message Authentication Code.pdf
- 哈尔滨工程大学:《计算机安全与密码学 Computer Security and Cryptography》课程教学资源(课件讲稿)序列密码 Sequential Cipher.pdf
- 哈尔滨工程大学:《计算机安全与密码学 Computer Security and Cryptography》课程教学资源(课件讲稿)分组密码 Block Cipher.pdf
- 安徽理工大学:《计算机安全与密码学 Computer Security and Cryptography》课程教学资源(课件讲稿)利用重合指数法破解Virginia加密 Breaking Virginia Encryption.pptx
- 哈尔滨工程大学:《计算机安全与密码学 Computer Security and Cryptography》课程教学资源(课件讲稿)传统密码技术 Classical cryptography.pdf
- 信息安全专业教学资源(讲稿)Introduction to Artificial Immune Systems(AIS).ppt
- 安徽理工大学:信息安全专业教学资源(讲稿)Differential Privacy.pdf
- 信息安全专业教学资源(讲稿)An Introduction to Artificial Immune Systems(ES2001).ppt
- 安徽理工大学:信息安全专业教学资源(讲稿)信息安全学科综述 An Overview of Information Security.ppt
- 安徽理工大学:信息安全专业教学资源(讲稿)信息安全专业介绍 An Introduction to Specialty in Information.ppt
- 信息安全专业教学资源(讲稿)Malware and Artificial Immune Systems.pdf
- Computational Intelligence(Concepts to Implementations)Part 1.pdf
- 安徽理工大学:《数据结构》课程教学资源(2016计算机网络课程设计任务书).doc
- 安徽理工大学:《数据结构》课程教学资源(2018计算机专业实习设计任务书).docx
- 安徽理工大学:《数据结构》课程教学资源(PPT课件讲稿,C语言版,2018)第1章 绪论(主讲:孙克雷).pptx
- 安徽理工大学:《数据结构》课程教学资源(PPT课件讲稿,C语言版,2018)第2章 线性表.pptx
- 安徽理工大学:《数据结构》课程教学资源(PPT课件讲稿,C语言版,2018)第3章 栈和队列.pptx
- 安徽理工大学:《数据结构》课程教学资源(PPT课件讲稿,C语言版,2018)第4章 串.pptx
- 安徽理工大学:《数据结构》课程教学资源(PPT课件讲稿,C语言版,2018)第5章 数组和广义表.pptx
- 安徽理工大学:《数据结构》课程教学资源(PPT课件讲稿,C语言版,2018)第6章 树和二叉树.pptx
- 安徽理工大学:《数据结构》课程教学资源(PPT课件讲稿,C语言版,2018)第7章 图.pptx
- 安徽理工大学:《数据结构》课程教学资源(PPT课件讲稿,C语言版,2018)第9章 查找.pptx
- 安徽理工大学:《数据结构》课程教学资源(PPT课件讲稿,C语言版,2018)第10章 排序.pptx
- 安徽理工大学:《数据结构》课程教学资源(课件讲稿,C语言版)第1章 绪论(主讲:孙克雷).pdf
- 安徽理工大学:《数据结构》课程教学资源(课件讲稿,C语言版)第2章 线性表.pdf
