安徽理工大学:信息安全专业教学资源(讲稿)Differential Privacy

In cryptography,differential privacy aims to provide means to maximize the accuracy of queries from statistical databases while minimizing the chances of identifying its records. ----Source from wikipedia
In cryptography, differential privacy aims to provide means to maximize the accuracy of queries from statistical databases while minimizing the chances of identifying its records. ----Source from wikipedia

Outline 1.Context 2.The Mechanisms of Privacy Preserving 3.Applications under Differential Privacy 4.Our Current Research Works
Outline 1. Context 2. The Mechanisms of Privacy Preserving 3. Applications under Differential Privacy 4. Our Current Research Works
P 1.Context
1.Context
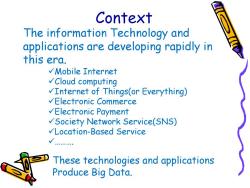
Context The information Technology and applications are developing rapidly in this era. √Mobile Internet √Cloud computing VInternet of Things(or Everything) √Electronic Commerce √Electronic Payment Society Network Service(SNS) Location-Based Service These technologies and applications Produce Big Data
Context The information Technology and applications are developing rapidly in this era. Mobile Internet Cloud computing Internet of Things(or Everything) Electronic Commerce Electronic Payment Society Network Service(SNS) Location-Based Service ………. These technologies and applications Produce Big Data
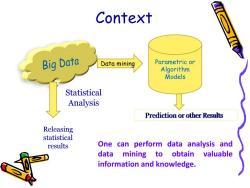
Context Big Data Data mining Parametric or Algorithm Models Statistical Analysis Prediction or other Results Releasing statistical results One can perform data analysis and data mining to obtain valuable information and knowledge
Context Parametric or Algorithm Models Data mining Statistical Analysis Releasing statistical results One can perform data analysis and data mining to obtain valuable information and knowledge
Context However,the disclosure of individual privacy and sensitive information is challenging when performing data release,data analysis or data mining
Context However, the disclosure of individual privacy and sensitive information is challenging when performing data release, data analysis or data mining

An simple example for statistical database incurring disclosure of sensitive information A dataset Query interface Name HIV indicator Tom f(n)=the count of Jack 1 the front of n recorders whose Henry 1 HIV indicator are 1. Diego Alice 1
Name HIV indicator Tom 0 Jack 1 Henry 1 Diego 0 Alice 1 …… ……. A dataset f(n)=the count of the front of n recorders whose HIV indicator are 1. Query interface An simple example for statistical database incurring disclosure of sensitive information

An example for statistical database The original dataset Histogram publication for the attribute age Name age HIV+indicator (Range count query) Tom 52 hiv+ Jack 43 1 6 Henry 21 1 5 Diego 41 3 5 Alice 54 1 2 3 贵第电 20-3030-4040-5050-6070- age Note:Suppose that the attacker know Alice's age is 54.He is also aware of the other patients'condition in bin 50-60 except Alice.He can infer whether Alice's HIV+is positive or not according to the above histogram publication
An example for statistical database Name age HIV+ indicator Tom 52 0 Jack 43 1 Henry 21 1 Diego 41 0 Alice 54 1 …… ……. The original dataset Histogram publication for the attribute age (Range count query) 1 2 1 3 5 0 1 2 3 4 5 6 20-30 30-40 40-50 50-60 70- hiv+ age Note: Suppose that the attacker know Alice’s age is 54. He is also aware of the other patients’ condition in bin 50-60 except Alice. He can infer whether Alice’s HIV+ is positive or not according to the above histogram publication

Context Summarily,the following operations s can all incur disclosure of individual identifiers or sensitive information: Providing the full database for analytics or data mining; Removing the personal identifiers(such as name, ID); ◆Giving the query/statistic/analysis interface program
Context Summarily, the following operations can all incur disclosure of individual identifiers or sensitive information: Providing the full database for analytics or data mining; Removing the personal identifiers(such as name, ID); Giving the query/statistic/analysis interface program

Context The events of disclosure of sensitive information: Patient specific data of 135,000 state employees and their families published by the Group insurance Commission (GIC)in Massachusetts; Anonymity Ethnicity Name Visit date Address ZIP Note:Latanya Diagnosis Date Birth Sweeney Broke this registered anonymized data and Procedure date found William Weld, Party the governor of Medication Sex affiliation Massachusetts at that time. Total charge Date last voted Medical Data Voter List
Context The events of disclosure of sensitive information: Patient specific data of 135,000 state employees and their families published by the Group insurance Commission (GIC) in Massachusetts; Note: Latanya Sweeney Broke this anonymized data and found William Weld, the governor of Massachusetts at that time. Anonymity
按次数下载不扣除下载券;
注册用户24小时内重复下载只扣除一次;
顺序:VIP每日次数-->可用次数-->下载券;
- 信息安全专业教学资源(讲稿)Introduction to Artificial Immune Systems(AIS).ppt
- 信息安全专业教学资源(讲稿)Artificial Immune Systems——An Emerging Technology.ppt
- 安徽理工大学:信息安全专业教学资源(讲稿)Bot、Botnet及其检测技术.pdf
- 安徽理工大学:信息安全专业教学资源(讲稿)Advance in Intrusion Detection Techniques.ppt
- 信息安全专业参考书籍:《Mathematics for Computer Science》计算机科学数学(revised Monday 5th June, 2017,Eric Lehman、F Thomson Leighton、Albert R Meyer).pdf
- 安徽理工大学:信息安全专业教学资源(讲稿)学科前沿讲座之一.pptx
- 安徽理工大学:《Linux开发基础 Development Foundation on Linux OS》课程教学资源(PPT课件讲稿)Section 4 Perl编程(附Perl源代码).ppt
- 安徽理工大学:《Linux开发基础 Development Foundation on Linux OS》课程教学资源(PPT课件讲稿)Section 4 Perl programming.ppt
- 清华大学出版社:《GNU/Linux编程指南》参考书籍【美】K. Wall,M. Watson, M. Whitis(共39章).pdf
- 安徽理工大学:《Linux开发基础 Development Foundation on Linux OS》课程教学资源(PPT课件讲稿)Section 2、3 GNU C/C++编程(CGI programming in GNU C/C++ language).ppt
- 安徽理工大学:《Linux开发基础 Development Foundation on Linux OS》课程教学资源(PPT课件讲稿)Section 1 Shell编程 Shell programming on Linux OS.ppt
- 清华大学出版社:《智能技术》课程教学资源(PPT课件讲稿)第8章 机器学习 machine learning.ppt
- 清华大学出版社:《智能技术》课程教学资源(PPT课件讲稿)第4章 模糊逻辑技术 fuzzy logic(编著:曹承志).ppt
- 清华大学出版社:《智能技术》课程教学资源(PPT课件讲稿)第6章 遗传算法(genetic algorithms,GA).ppt
- 安徽理工大学:《计算机安全与密码学 Computer Security and Cryptography》课程教学资源(课件讲稿)密钥管技术理 Key Management.pdf
- 哈尔滨工程大学:《计算机安全与密码学 Computer Security and Cryptography》课程教学资源(课件讲稿)数字签名技术 Digital Signature.pdf
- 哈尔滨工程大学:《计算机安全与密码学 Computer Security and Cryptography》课程教学资源(课件讲稿)公钥密码体制 Public Key Cryptography.pdf
- 哈尔滨工程大学:《计算机安全与密码学 Computer Security and Cryptography》课程教学资源(课件讲稿)散列函数与消息认证码 Hash and Message Authentication Code.pdf
- 哈尔滨工程大学:《计算机安全与密码学 Computer Security and Cryptography》课程教学资源(课件讲稿)序列密码 Sequential Cipher.pdf
- 哈尔滨工程大学:《计算机安全与密码学 Computer Security and Cryptography》课程教学资源(课件讲稿)分组密码 Block Cipher.pdf
- 信息安全专业教学资源(讲稿)An Introduction to Artificial Immune Systems(ES2001).ppt
- 安徽理工大学:信息安全专业教学资源(讲稿)信息安全学科综述 An Overview of Information Security.ppt
- 安徽理工大学:信息安全专业教学资源(讲稿)信息安全专业介绍 An Introduction to Specialty in Information.ppt
- 信息安全专业教学资源(讲稿)Malware and Artificial Immune Systems.pdf
- Computational Intelligence(Concepts to Implementations)Part 1.pdf
- 安徽理工大学:《数据结构》课程教学资源(2016计算机网络课程设计任务书).doc
- 安徽理工大学:《数据结构》课程教学资源(2018计算机专业实习设计任务书).docx
- 安徽理工大学:《数据结构》课程教学资源(PPT课件讲稿,C语言版,2018)第1章 绪论(主讲:孙克雷).pptx
- 安徽理工大学:《数据结构》课程教学资源(PPT课件讲稿,C语言版,2018)第2章 线性表.pptx
- 安徽理工大学:《数据结构》课程教学资源(PPT课件讲稿,C语言版,2018)第3章 栈和队列.pptx
- 安徽理工大学:《数据结构》课程教学资源(PPT课件讲稿,C语言版,2018)第4章 串.pptx
- 安徽理工大学:《数据结构》课程教学资源(PPT课件讲稿,C语言版,2018)第5章 数组和广义表.pptx
- 安徽理工大学:《数据结构》课程教学资源(PPT课件讲稿,C语言版,2018)第6章 树和二叉树.pptx
- 安徽理工大学:《数据结构》课程教学资源(PPT课件讲稿,C语言版,2018)第7章 图.pptx
- 安徽理工大学:《数据结构》课程教学资源(PPT课件讲稿,C语言版,2018)第9章 查找.pptx
- 安徽理工大学:《数据结构》课程教学资源(PPT课件讲稿,C语言版,2018)第10章 排序.pptx
- 安徽理工大学:《数据结构》课程教学资源(课件讲稿,C语言版)第1章 绪论(主讲:孙克雷).pdf
- 安徽理工大学:《数据结构》课程教学资源(课件讲稿,C语言版)第2章 线性表.pdf
- 安徽理工大学:《数据结构》课程教学资源(课件讲稿,C语言版)第3章 栈和队列.pdf
- 安徽理工大学:《数据结构》课程教学资源(课件讲稿,C语言版)第4章 串.pdf
