安徽理工大学:信息安全专业教学资源(讲稿)Advance in Intrusion Detection Techniques

Advance in Intrusion Detection Techniques Associate Prof.Fang Xianjin(方贤进) Computer Science Engineering SchoolofAUST
Advance in Intrusion Detection Techniques Associate Prof. Fang Xianjin(方贤进) Computer Science & Engineering School of AUST

Outline Context of computer security problem ● Brief summaries of computer security system What is IDS? Architecture and Classification of IDS Intrusion detection techniques My current research works Questions and answer
Outline ⚫ Context of computer security problem ⚫ Brief summaries of computer security system ⚫ What is IDS? ⚫ Architecture and Classification of IDS ⚫ Intrusion detection techniques ⚫ My current research works ⚫ Questions and answer
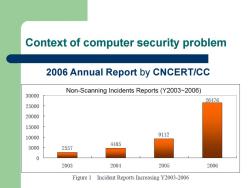
Context of computer security problem 2006 Annual Report by CNCERT/CC Non-Scanning Incidents Reports(Y2003~2006) 30000 26476 25000 20000 15000 10000 9112 4485 5000 2557 0 2003 2004 2005 2006 Figure 1 Incident Reports Increasing Y2003-2006
Context of computer security problem 2006 Annual Report by CNCERT/CC
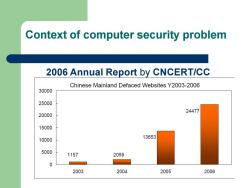
Context of computer security problem 2006 Annual Report by CNCERT/CC Chinese Mainland Defaced Websites Y2003-2006 30000 25000 24477 20000 15000 10000 13653 5000 1157 2059 0 2003 2004 2005 2006
Context of computer security problem 2006 Annual Report by CNCERT/CC
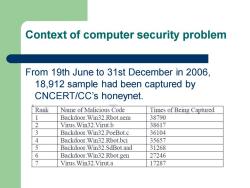
Context of computer security problem From 19th June to 31st December in 2006. 18,912 sample had been captured by CNCERT/CC's honeynet. Rank Name of Malicious Code Times of Being Captured 1 Backdoor.Win32.Rbot.aem 38790 2 Virus.Win32.Virut.b 38617 3 Backdoor.Win32.PoeBot.c 36104 4 Backdoor.Win32.Rbot.bci 35657 5 Backdoor.Win32.SdBot.aad 31268 6 Backdoor.Win32.Rbot.gen 27246 Virus.Win32.Virut.a 17287
Context of computer security problem From 19th June to 31st December in 2006, 18,912 sample had been captured by CNCERT/CC’s honeynet

Brief summaries of computer security system Multi-layer defense: First layer is static access mechanisms, such as passwords and file permissions. Disadvantages: Limited to provide comprehensive security; Overly restrictive for legitimate users of computer system;
Brief summaries of computer security system Multi-layer defense: ⚫ First layer is static access mechanisms, such as passwords and file permissions. Disadvantages: — Limited to provide comprehensive security; — Overly restrictive for legitimate users of computer system;

Brief summaries of computer security system Multi-layer defense: second layer is cryptography,which is used for providing secure channels and host authentication Another layer is firewall,which filters out undesirable network traffic in a network system
Brief summaries of computer security system Multi-layer defense: ⚫ second layer is cryptography, which is used for providing secure channels and host authentication ⚫ Another layer is firewall, which filters out undesirable network traffic in a network system

Brief summaries of computer security system Multi-layer defense: The latest layer of defense is provided by dynamic protection systems that can detect and prevent intrusion,namely,is known as Intrusion Detection System(IDS)
Brief summaries of computer security system Multi-layer defense: ⚫ The latest layer of defense is provided by dynamic protection systems that can detect and prevent intrusion, namely, is known as Intrusion Detection System(IDS)

What is IDS? Mathematical description for IDS: U:universe set, S:normal/legitimate/acceptable pattern set (self set ) N:anomalous/illegitimate/unacceptable pattern set(nonself set), SUN=U,S∩N=Φ False IDS=(f,M),f is a nonlinear classification function,M is positives detection range of detection system, U f:U*×U→{normal,anomalous? Nonself normal,S∈M Self f(M,s)= False anomalous,otherwise negatives
What is IDS? Mathematical description for IDS: U:universe set, S: normal/legitimate/acceptable pattern set (self set ), N: anomalous/illegitimate/unacceptable pattern set (nonself set), S∪N=U, S∩N=Ф IDS=(f, M), f is a nonlinear classification function, M is detection range of detection system, f: U*×U→{normal, anomalous} = anomalous otherwise normal s M f M s , , ( , ) Nonself Self False positives False negatives M U
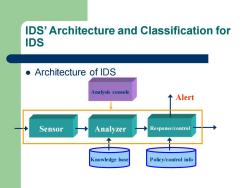
IDS'Architecture and Classification for IDS ●Architecture of IDS Analysis console 个 Alert Sensor Analyzer Response/control Knowledge base Policy/control info
IDS’ Architecture and Classification for IDS ⚫ Architecture of IDS Sensor Analyzer Knowledge base Response/control Policy/control info Alert Analysis console
按次数下载不扣除下载券;
注册用户24小时内重复下载只扣除一次;
顺序:VIP每日次数-->可用次数-->下载券;
- 信息安全专业参考书籍:《Mathematics for Computer Science》计算机科学数学(revised Monday 5th June, 2017,Eric Lehman、F Thomson Leighton、Albert R Meyer).pdf
- 安徽理工大学:信息安全专业教学资源(讲稿)学科前沿讲座之一.pptx
- 安徽理工大学:《Linux开发基础 Development Foundation on Linux OS》课程教学资源(PPT课件讲稿)Section 4 Perl编程(附Perl源代码).ppt
- 安徽理工大学:《Linux开发基础 Development Foundation on Linux OS》课程教学资源(PPT课件讲稿)Section 4 Perl programming.ppt
- 清华大学出版社:《GNU/Linux编程指南》参考书籍【美】K. Wall,M. Watson, M. Whitis(共39章).pdf
- 安徽理工大学:《Linux开发基础 Development Foundation on Linux OS》课程教学资源(PPT课件讲稿)Section 2、3 GNU C/C++编程(CGI programming in GNU C/C++ language).ppt
- 安徽理工大学:《Linux开发基础 Development Foundation on Linux OS》课程教学资源(PPT课件讲稿)Section 1 Shell编程 Shell programming on Linux OS.ppt
- 清华大学出版社:《智能技术》课程教学资源(PPT课件讲稿)第8章 机器学习 machine learning.ppt
- 清华大学出版社:《智能技术》课程教学资源(PPT课件讲稿)第4章 模糊逻辑技术 fuzzy logic(编著:曹承志).ppt
- 清华大学出版社:《智能技术》课程教学资源(PPT课件讲稿)第6章 遗传算法(genetic algorithms,GA).ppt
- 安徽理工大学:《计算机安全与密码学 Computer Security and Cryptography》课程教学资源(课件讲稿)密钥管技术理 Key Management.pdf
- 哈尔滨工程大学:《计算机安全与密码学 Computer Security and Cryptography》课程教学资源(课件讲稿)数字签名技术 Digital Signature.pdf
- 哈尔滨工程大学:《计算机安全与密码学 Computer Security and Cryptography》课程教学资源(课件讲稿)公钥密码体制 Public Key Cryptography.pdf
- 哈尔滨工程大学:《计算机安全与密码学 Computer Security and Cryptography》课程教学资源(课件讲稿)散列函数与消息认证码 Hash and Message Authentication Code.pdf
- 哈尔滨工程大学:《计算机安全与密码学 Computer Security and Cryptography》课程教学资源(课件讲稿)序列密码 Sequential Cipher.pdf
- 哈尔滨工程大学:《计算机安全与密码学 Computer Security and Cryptography》课程教学资源(课件讲稿)分组密码 Block Cipher.pdf
- 安徽理工大学:《计算机安全与密码学 Computer Security and Cryptography》课程教学资源(课件讲稿)利用重合指数法破解Virginia加密 Breaking Virginia Encryption.pptx
- 哈尔滨工程大学:《计算机安全与密码学 Computer Security and Cryptography》课程教学资源(课件讲稿)传统密码技术 Classical cryptography.pdf
- 安徽理工大学:《计算机安全与密码学 Computer Security and Cryptography》课程教学资源(课件讲稿)Preliminary knowledge.pptx
- 《计算机安全与密码学 Computer Security and Cryptography》课程教学资源(课件讲稿)2020年上半年我国互联网网络安全监测数据分析报告.pdf
- 安徽理工大学:信息安全专业教学资源(讲稿)Bot、Botnet及其检测技术.pdf
- 信息安全专业教学资源(讲稿)Artificial Immune Systems——An Emerging Technology.ppt
- 信息安全专业教学资源(讲稿)Introduction to Artificial Immune Systems(AIS).ppt
- 安徽理工大学:信息安全专业教学资源(讲稿)Differential Privacy.pdf
- 信息安全专业教学资源(讲稿)An Introduction to Artificial Immune Systems(ES2001).ppt
- 安徽理工大学:信息安全专业教学资源(讲稿)信息安全学科综述 An Overview of Information Security.ppt
- 安徽理工大学:信息安全专业教学资源(讲稿)信息安全专业介绍 An Introduction to Specialty in Information.ppt
- 信息安全专业教学资源(讲稿)Malware and Artificial Immune Systems.pdf
- Computational Intelligence(Concepts to Implementations)Part 1.pdf
- 安徽理工大学:《数据结构》课程教学资源(2016计算机网络课程设计任务书).doc
- 安徽理工大学:《数据结构》课程教学资源(2018计算机专业实习设计任务书).docx
- 安徽理工大学:《数据结构》课程教学资源(PPT课件讲稿,C语言版,2018)第1章 绪论(主讲:孙克雷).pptx
- 安徽理工大学:《数据结构》课程教学资源(PPT课件讲稿,C语言版,2018)第2章 线性表.pptx
- 安徽理工大学:《数据结构》课程教学资源(PPT课件讲稿,C语言版,2018)第3章 栈和队列.pptx
- 安徽理工大学:《数据结构》课程教学资源(PPT课件讲稿,C语言版,2018)第4章 串.pptx
- 安徽理工大学:《数据结构》课程教学资源(PPT课件讲稿,C语言版,2018)第5章 数组和广义表.pptx
- 安徽理工大学:《数据结构》课程教学资源(PPT课件讲稿,C语言版,2018)第6章 树和二叉树.pptx
- 安徽理工大学:《数据结构》课程教学资源(PPT课件讲稿,C语言版,2018)第7章 图.pptx
- 安徽理工大学:《数据结构》课程教学资源(PPT课件讲稿,C语言版,2018)第9章 查找.pptx
- 安徽理工大学:《数据结构》课程教学资源(PPT课件讲稿,C语言版,2018)第10章 排序.pptx
