福州大学:《计算机网络管理》课程PPT教学课件(英文)Chapter 13 Network Management Applications

Chapter13 Network Management Applications The management of networked information services involves both network and system resources.OSI defines network management as a five-layer architecture.We extended the model to include system management and present the integrated architecture in Figure 13.1: L5 business management L4 Service management L3 network management or system management L2 element management or resource management LI network elements and system resources
Chapter13 Network Management Applications The management of networked information services involves both network and system resources. OSI defines network management as a five-layer architecture. We extended the model to include system management and present the integrated architecture in Figure 13.1: L5 business management L4 Service management L3 network management or system management L2 element management or resource management L1 network elements and system resources

13.1 Configuration Management Configuration management in network management is normally used in the context of discovering network topology, mapping the network,and setting up configuration parameters in management agents and management systems.Network management in the broad sense also includes network provisioning,which includes network planning and design. Network provisioning is considered to be part of configuration management
13.1 Configuration Management Configuration management in network management is normally used in the context of discovering network topology, mapping the network, and setting up configuration parameters in management agents and management systems. Network management in the broad sense also includes network provisioning, which includes network planning and design. Network provisioning is considered to be part of configuration management

13.1.1 Network Provisioning Network provisioning,also called circuit provisioning in the telephone industry,is an automated process.A trunk (circuit from the originating switching center to the destination switching center)and a special service circuit (customized to meet customer specifications)are designed by application programs written in operation systems,Planning and inventory systems are integrated with design systems to build an overall system.Thus a circuit designed for the future automatically derives its turn-on date from the planning system and ensures that the components are available in the inventory system
13.1.1 Network Provisioning Network provisioning, also called circuit provisioning in the telephone industry, is an automated process. A trunk (circuit from the originating switching center to the destination switching center) and a special service circuit (customized to meet customer specifications) are designed by application programs written in operation systems, Planning and inventory systems are integrated with design systems to build an overall system. Thus a circuit designed for the future automatically derives its turn-on date from the planning system and ensures that the components are available in the inventory system

13.1.2 Inventory Management An efficient database system is an essential part of an inventory management system.We need to be aware of the specification details associated with various components.The data should be accessible by means of different indices. Some of the obvious indices or access keys are the component description or part number,components that match a set of characteristics,components in use and in spare,and components to be freed-up for future use
13.1.2 Inventory Management An efficient database system is an essential part of an inventory management system. We need to be aware of the specification details associated with various components. The data should be accessible by means of different indices. Some of the obvious indices or access keys are the component description or part number, components that match a set of characteristics, components in use and in spare, and components to be freed-up for future use

13.1.3 Network Topology Network management is based on knowledge of network topology.As a network grows, shrinks,or otherwise changes,network topology needs to be updated automatically. Such updating is done by the discovery application in the network management system.However,the scope of the discovery process needs to be constrained.For example, the arp command can discover any network component that responds with an IP address, which can then be mapped by the network management system.If the response includes workstations that are turned on only when they are in use,the network management system would indicate failure whenever they are off.Obviously,that is not desirable
13.1.3 Network Topology Network management is based on knowledge of network topology. As a network grows, shrinks, or otherwise changes, network topology needs to be updated automatically. Such updating is done by the discovery application in the network management system. However, the scope of the discovery process needs to be constrained. For example, the arp command can discover any network component that responds with an IP address, which can then be mapped by the network management system. If the response includes workstations that are turned on only when they are in use, the network management system would indicate failure whenever they are off. Obviously, that is not desirable
Chapter13 Network Management Applications Autodiscovery can be done by using the broadcast ping on each segment and following up with further SNMP queries to gather more details on the system.A more efficient method is to look at the ARP cache in the local router.The ARP cache table is large and contains the addresses of all the hosts and nodes used in recent communications.Use of this table also allows subsequent ARP queries to be sent to other routers.This process is continued until the desired information is obtained on all IP addresses defined I by the scope of the autodiscovery procedure
Chapter13 Network Management Applications Autodiscovery can be done by using the broadcast ping on each segment and following up with further SNMP queries to gather more details on the system. A more efficient method is to look at the ARP cache in the local router. The ARP cache table is large and contains the addresses of all the hosts and nodes used in recent communications. Use of this table also allows subsequent ARP queries to be sent to other routers.This process is continued until the desired information is obtained on all IP addresses defined by the scope of the autodiscovery procedure
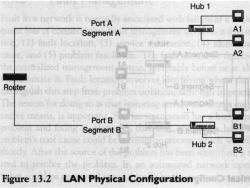
Hub 1 Port A Segment A Router Port B Segment B 口口 Hub 2 source of th se B2 Figure 13.2 LAN Physical Configuration
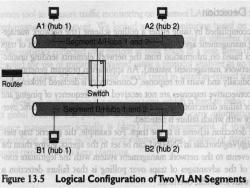
A1 (hub 1) A2(hub 2) B50908) Router Switch baviso9T jon 916 asanodasT 9viuogano B1 (hub 1) B2(hub 2) Figure 13.5 Logical Configuration of Two VLAN Segments

13.3 Performance Management Network performance is a nebulous term,which is hard to define or quantify in terms of global metrics.Performance management actually is (data) traffic management.It involves following data monitoring,problem isolation,performance tuning, analysis of statistical data for recognizing trends, and resource planning. 13.3.1 Performance Metrics The parameters that can be attributed to defining network performance on a global level are throughput,response time,network availability, and network reliability.The metrics of these parameters depend on what,when,and where the measurements are made
13.3 Performance Management Network performance is a nebulous term, which is hard to define or quantify in terms of global metrics. Performance management actually is (data) traffic management. It involves following data monitoring, problem isolation, performance tuning, analysis of statistical data for recognizing trends, and resource planning. 13.3.1 Performance Metrics The parameters that can be attributed to defining network performance on a global level are throughput, response time, network availability, and network reliability. The metrics of these parameters depend on what, when, and where the measurements are made
13.3.2 Data Monitoring Data monitoring in the network for abnormal performance behavior,such as a high collision rate in an Ethernet LAN and excessive packet drop because of overload,are detected by traps generated by agents and RMON.Performance-related issues are detected primarily with trap messages generated by RMON probes.Thresholds are s set for important SNMP parameters in the RMON,which then generate alarms when the preset thresholds are crossed.For example,the parameters in the alarm group and the event group in the RMON MIB [RFC 1757]may be set for the object identifier to be monitored.The time interval over which the data are to be collected for calculation and the rising and falling thresholds are specified
13.3.2 Data Monitoring Data monitoring in the network for abnormal performance behavior, such as a high collision rate in an Ethernet LAN and excessive packet drop because of overload, are detected by traps generated by agents and RMON. Performance-related issues are detected primarily with trap messages generated by RMON probes. Thresholds are set for important SNMP parameters in the RMON, which then generate alarms when the preset thresholds are crossed. For example, the parameters in the alarm group and the event group in the RMON MIB [RFC 1757] may be set for the object identifier to be monitored. The time interval over which the data are to be collected for calculation and the rising and falling thresholds are specified
按次数下载不扣除下载券;
注册用户24小时内重复下载只扣除一次;
顺序:VIP每日次数-->可用次数-->下载券;
- 福州大学:《计算机网络管理》课程PPT教学课件(英文)Chapter 8 RMON.ppt
- 福州大学:《计算机网络管理》课程PPT教学课件(英文)Chapter 7 SNMPv3.ppt
- 福州大学:《计算机网络管理》课程PPT教学课件(英文)Chapter 6 SNMP Management-SNMPv2.ppt
- 福州大学:《计算机网络管理》课程PPT教学课件(英文)Chapter 5 SNMPv1 Network Management Communication and Functional Models.ppt
- 福州大学:《计算机网络管理》课程PPT教学课件(英文)Chapter 4 SNMPv1-Organization and Information Models.ppt
- 福州大学:《计算机网络管理》课程PPT教学课件(英文)Chapter 3 Basic Foundations Standards, Models and Language.ppt
- 福州大学:《计算机网络管理》课程PPT教学课件(英文)Chapter 14 Web-Based Management.ppt
- 福州大学:《计算机网络管理》课程PPT教学课件(英文)Chapter 12 Tools and Systems.ppt
- 新疆大学:《微机原理与接口技术》课程教学资源(PPT课件)第五章 微处理器的硬件特性.ppt
- 新疆大学:《微机原理与接口技术》课程教学资源(PPT课件)第六章 内存储器接口.ppt
- 新疆大学:《微机原理与接口技术》课程教学资源(PPT课件)第三章 汇编语言.ppt
- 新疆大学:《微机原理与接口技术》课程教学资源(PPT课件)第七章 总线.ppt
- 新疆大学:《微机原理与接口技术》课程教学资源(PPT课件)第九章 键盘技术和LED.ppt
- 新疆大学:《微机原理与接口技术》课程教学资源(PPT课件)第十章 数模和模数转换器.ppt
- 新疆大学:《微机原理与接口技术》课程教学资源(PPT课件)第二章 微处理器存储器管理技术.ppt
- 新疆大学:《微机原理与接口技术》课程教学资源(PPT课件)第一章 微型计算机系统概述(负责人:袁保社).ppt
- 新疆大学:《微机原理与接口技术》课程教学资源(参考资料)教师手则部分内容.doc
- 新疆大学:《微机原理与接口技术》课程教学资源(参考资料)补充教材.doc
- 新疆大学:《微机原理与接口技术》课程教学大纲(简编).pdf
- 《计算机与信息技术基础》课程PPT教学课件(第4版)第12章 计算机组装与维护.pptx
- 《ASP网络程序设计》课程教学资源(试卷习题)课后习题及参考答案1.doc
- 《ASP网络程序设计》课程教学资源(试卷习题)课后习题及参考答案2.doc
- 《ASP网络程序设计》课程教学资源(试卷习题)课后习题及参考答案3.doc
- 《ASP网络程序设计》课程教学资源(试卷习题)课后习题及参考答案4.doc
- 《ASP网络程序设计》课程教学资源(试卷习题)课后习题及参考答案5.doc
- 《ASP网络程序设计》课程教学资源(试卷习题)课后习题及参考答案6.doc
- 海南大学:《计算机辅助设计》课程实验教学大纲 Computer aided design.doc
- 海南大学:《计算机辅助设计》课程授课教案.doc
- 福建交通职业技术学院:《计算机网络基础》课程教学资源(教案讲义)网络技术与应用实务01.doc
- 福建交通职业技术学院:《计算机网络基础》课程教学资源(教案讲义)网络技术与应用实务10.doc
- 福建交通职业技术学院:《计算机网络基础》课程教学资源(教案讲义)网络技术与应用实务02.doc
- 福建交通职业技术学院:《计算机网络基础》课程教学资源(教案讲义)网络技术与应用实务03.doc
- 福建交通职业技术学院:《计算机网络基础》课程教学资源(教案讲义)网络技术与应用实务04.doc
- 福建交通职业技术学院:《计算机网络基础》课程教学资源(教案讲义)网络技术与应用实务05.doc
- 福建交通职业技术学院:《计算机网络基础》课程教学资源(教案讲义)网络技术与应用实务06.doc
- 福建交通职业技术学院:《计算机网络基础》课程教学资源(教案讲义)网络技术与应用实务07.doc
- 福建交通职业技术学院:《计算机网络基础》课程教学资源(教案讲义)网络技术与应用实务08.doc
- 福建交通职业技术学院:《计算机网络基础》课程教学资源(教案讲义)网络技术与应用实务09.doc
- 福建交通职业技术学院:《计算机网络基础》课程教学资源(实验指导)DHCP服务器的安装与配置.doc
- 福建交通职业技术学院:《计算机网络基础》课程教学资源(实验指导)FTP服务器的安装及配置.doc
