Asymptotic Analysis on Secrecy Capacity in Large-Scale Wireless Networks

上游充通大¥ SHANGHAI JIAO TONG UNIVERSITY Asymptotic Analysis on Secrecy Capacity in Large-Scale Wireless Networks Jinbei Zhang,Luoyifu,Xinbing Wang Department of Electronic Engineering Shanghai Jiao Tong University Aug.13,2013
Asymptotic Analysis on Secrecy Capacity in Large-Scale Wireless Networks Jinbei Zhang, Luoyifu, Xinbing Wang Department of Electronic Engineering Shanghai Jiao Tong University Aug. 13, 2013

Outline 上浒充通大¥ SHANGHAI JIAO TONG UNIVERSITY ▣Introduction Motivations Related works >Objectives Q Network Modeland Definition QSecrecy Capacity for Independent Eavesdroppers QSecrecy Capacity for Colluding Eavesdroppers ▣Discussion Q Conclusion and Future Work Asymptotic Analysis on Secrecy Capacity in Large-Scale Wireless Networks 2
Asymptotic Analysis on Secrecy Capacity in Large-Scale Wireless Networks 2 Outline ❑ Introduction ➢ Motivations ➢ Related works ➢ Objectives ❑ Network Model and Definition ❑ Secrecy Capacity for Independent Eavesdroppers ❑ Secrecy Capacity for Colluding Eavesdroppers ❑ Discussion ❑ Conclusion and Future Work

Motivations 上浒充通大粤 SHANGHAI JIAO TONG UNIVERSITY Secrecy is a Major Concern in Wireless Networks. >Mobile Phone Wallet Military networks CARD HERE Asymptotic Analysis on Secrecy Capacity in Large-Scale Wireless Networks 3
3 Motivations ❑ Secrecy is a Major Concern in Wireless Networks. ➢ Mobile Phone Wallet ➢ Military networks ➢ … Asymptotic Analysis on Secrecy Capacity in Large-Scale Wireless Networks
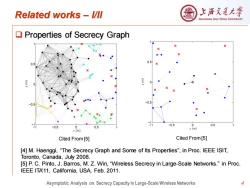
Related works l/ll 上浒充通大 SHANGHAI JIAO TONG UNIVERSITY Properties of Secrecy Graph + 0.5 ● 0.5 ● ● -0.5 -0.5 0 -0.5 0 0.5 -0.5 0.5 (m) z(m) Cited From [5] Cited From [5] [4]M.Haenggi,"The Secrecy Graph and Some of Its Properties",in Proc.IEEE ISIT, Toronto,Canada,July 2008. [5]P.C.Pinto,J.Barros,M.Z.Win,"Wireless Secrecy in Large-Scale Networks."in Proc. IEEE ITA11,California,USA,Feb.2011. Asymptotic Analysis on Secrecy Capacity in Large-Scale Wireless Networks 4
4 Related works – I/II ❑ Properties of Secrecy Graph [4] M. Haenggi, “The Secrecy Graph and Some of Its Properties”, in Proc. IEEE ISIT, Toronto, Canada, July 2008. [5] P. C. Pinto, J. Barros, M. Z. Win, “Wireless Secrecy in Large-Scale Networks.” in Proc. IEEE ITA’11, California, USA, Feb. 2011. Cited From [5] Cited From [5] Asymptotic Analysis on Secrecy Capacity in Large-Scale Wireless Networks

Related works ll/lI 上浒充通大 SHANGHAI JIAO TONG UNIVERSITY Secrecy Capacity in large-scale networks, Mobile Networks [16] Guard Zone [13] Artificial Noise+Fading Gain(CSI needed)[12] Cited from [12] [16]Y.Liang,H.V.Poor and L.Ying,"Secrecy Throughput of MANETs under Passive and Active Attacks",in IEEE Trans.Inform.Theory,Vol.57,No.10,Oct.2011. [13]O.Koyluoglu,E.Koksal,E.Gammel,"On Secrecy Capacity Scaling in Wireless Networks",submitted to IEEE Trans.Inform.Theory,Apr.2010. [12]S.Vasudevan,D.Goeckel and D.Towsley,"Security-capacity Trade-off in Large Wireless Networks using Keyless Secrecy",in Proc.ACM MobiHoc,Chicago,Illinois,USA, Sept.2010. Asymptotic Analysis on Secrecy Capacity in Large-Scale Wireless Networks 5
5 Related works – II/II ❑ Secrecy Capacity in large-scale networks, ➢ Mobile Networks [16] ➢ Guard Zone [13] ➢ Artificial Noise+Fading Gain(CSI needed) [12] [16] Y. Liang, H. V. Poor and L. Ying, “Secrecy Throughput of MANETs under Passive and Active Attacks”, in IEEE Trans. Inform. Theory, Vol. 57, No. 10, Oct. 2011. [13] O. Koyluoglu, E. Koksal, E. Gammel, “On Secrecy Capacity Scaling in Wireless Networks”, submitted to IEEE Trans. Inform. Theory, Apr. 2010. [12] S. Vasudevan, D. Goeckel and D. Towsley, “Security-capacity Trade-off in Large Wireless Networks using Keyless Secrecy”, in Proc. ACM MobiHoc, Chicago, Illinois, USA, Sept. 2010. Cited from [12] Asymptotic Analysis on Secrecy Capacity in Large-Scale Wireless Networks

Objectives 上游充通大学 SHANGHAI JIAO TONG UNIVERSITY Several questions arise: CSI information is difficult to obtain Artificial noises also degrade legitimate receivers'channels >Cost on capacity is quite large to utilize fading gain How to effectively improve the secrecy capacity? Asymptotic Analysis on Secrecy Capacity in Large-Scale Wireless Networks 6
6 Objectives ❑ Several questions arise: ➢ CSI information is difficult to obtain ➢ Artificial noises also degrade legitimate receivers’ channels ➢ Cost on capacity is quite large to utilize fading gain How to effectively improve the secrecy capacity? Asymptotic Analysis on Secrecy Capacity in Large-Scale Wireless Networks

Outline 上浒充通大学 SHANGHAI JIAO TONG UNIVERSITY ▣Introduction QNetwork Model and Definition QSecrecy Capacity for Independent Eavesdroppers QSecrecy Capacity for Colluding Eavesdroppers ▣Discussion Conclusion and Future Work Asymptotic Analysis on Secrecy Capacity in Large-Scale Wireless Networks 7
7 Outline ❑ Introduction ❑ Network Model and Definition ❑ Secrecy Capacity for Independent Eavesdroppers ❑ Secrecy Capacity for Colluding Eavesdroppers ❑ Discussion ❑ Conclusion and Future Work Asymptotic Analysis on Secrecy Capacity in Large-Scale Wireless Networks
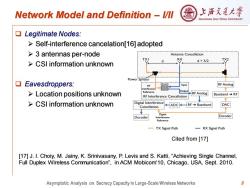
Network Model and Definition l/ll 上浒充通大 SHANGHAI JIAO TONG UNIVERSITY ▣Legitimate Nodes. >Self-interference cancelation[16]adopted >3 antennas per-node Antenna Cancellation TX RX d+λ/2 CSI information unknown Power Splitter ▣Eavesdroppers. OHx220 RF Input RF Analog Interference 个 Location positions unknown Reference Output! RF Analog Baseband→RF RF Interference Cancellation 个 CSI information unknown Digital Interference Cancellation ADC RF>Baseband DAC Digital Decoder Interference Encoder Reference TX Signal Path 一RX Signal Path Cited from [17] [17]J.I.Choiy,M.Jainy,K.Srinivasany,P.Levis and S.Katti,"Achieving Single Channel, Full Duplex Wireless Communication",in ACM Mobicom'10,Chicago,USA,Sept.2010. Asymptotic Analysis on Secrecy Capacity in Large-Scale Wireless Networks 8
8 Network Model and Definition – I/II ❑ Legitimate Nodes: ➢ Self-interference cancelation[16] adopted ➢ 3 antennas per-node ➢ CSI information unknown ❑ Eavesdroppers: ➢ Location positions unknown ➢ CSI information unknown Cited from [17] [17] J. I. Choiy, M. Jainy, K. Srinivasany, P. Levis and S. Katti, “Achieving Single Channel, Full Duplex Wireless Communication”, in ACM Mobicom’10, Chicago, USA, Sept. 2010. Asymptotic Analysis on Secrecy Capacity in Large-Scale Wireless Networks

Network Model and Definition ll/ll 上洋充通大学 SHANGHAI JIAO TONG UNIVERSITY ▣Network Model: Extended networks: n nodes randomly distributed in a network with size n. Static >Physical channel model Pl(;x;) SNR,+∑rP4(x,+2P】 PI(xx) SINR.N+∑nP)+2x,) where I(xx)=min(1,d) Definition of secrecy capacity Ri=Ry-Re log2 (1+SINR )-log2 (1+SINRie) where SINR=maxce:SINR Asymptotic Analysis on Secrecy Capacity in Large-Scale Wireless Networks 9
9 Network Model and Definition – II/II ❑ Network Model: ➢ Extended networks: n nodes randomly distributed in a network with size n. ➢ Static ➢ Physical channel model where ➢ Definition of secrecy capacity 0 \{ } \{ } ( , ) ( , ) ( , ) t i j ij t k j r k j k T i k R i Pl x x SINR N Pl x x Pl x x = + + 0 \{ } ( , ) ( , ) ( , ) t i e ie t k e r k e k T i k R Pl x x SINR N Pl x x Pl x x = + + ( , ) min(1, ) i j ij l x x d − = 2 2 log (1 ) log (1 ) s R R R SINR SINR ij ij ie ij ie = − = + − + max ie e ie SINR SINR = where Asymptotic Analysis on Secrecy Capacity in Large-Scale Wireless Networks

Outline 上浒充通大¥ SHANGHAI JIAO TONG UNIVERSITY ▣Introduction Q Network Modeland Definition ▣ Secrecy Capacity for Independent Eavesdroppers >Lower Bound >Upper Bound QSecrecy Capacity for Colluding Eavesdroppers ▣Discussion Q Conclusion and Future Work Asymptotic Analysis on Secrecy Capacity in Large-Scale Wireless Networks 10
10 Outline ❑ Introduction ❑ Network Model and Definition ❑ Secrecy Capacity for Independent Eavesdroppers ➢ Lower Bound ➢ Upper Bound ❑ Secrecy Capacity for Colluding Eavesdroppers ❑ Discussion ❑ Conclusion and Future Work Asymptotic Analysis on Secrecy Capacity in Large-Scale Wireless Networks
按次数下载不扣除下载券;
注册用户24小时内重复下载只扣除一次;
顺序:VIP每日次数-->可用次数-->下载券;
- Asymptotic Analysis on Secrecy Capacity in Large-Scale Wireless Networks.pdf
- Mobility Increases the Connectivity of Wireless Networks.pdf
- Capacity Scaling of General Cognitive Networks.pdf
- Multicast Performance With Hierarchical Cooperation.pdf
- Delay and Capacity Tradeoff Analysis for MotionCast.pdf
- Achieving 100% Throughput in TCP/AQM Under Aggressive Packet Marking With Small Buffer.pdf
- DRIMUX:Dynamic Rumor Influence Minimization with User Experience in Social Networks.pdf
- Coverage and Energy Consumption Control in Mobile Heterogeneous Wireless Sensor Networks.pdf
- Optimal Determination of Source-destination Connectivity in Random Graphs.ppt
- MotionCast:On the Capacity and Delay Tradeoffs.ppt
- Fundamental Relationship between Node Density and Delay in Wireless Ad Hoc Networks with Unreliable Links.ppt
- Mobility Increases the Connectivity of K-hop Clustered Wireless Networks.ppt
- Heterogeneity Increases Multicast Capacity In Clustered Network.ppt
- Throughput and Delay Scaling of General Cognitive Networks.pdf
- Determining Source-Destination Connectivity in Uncertain Networks:Modeling and Solutions.pdf
- Joint Optimization of Multicast Energy in Delay-constrained Mobile Wireless Networks.pdf
- FINE:A Framework for Distributed Learning on Incomplete Observations for Heterogeneous Crowdsensing Networks.pdf
- A Distributed Algorithm to Construct Multicast Trees in WSNs:An Approximate Steiner Tree Approach.pptx
- Distributed Multicast Tree Construction in Wireless Sensor Networks.pdf
- Coded Caching under Arbitrary Popularity Distributions.pptx
- Multicast Capacity with Max-Min Fairness for Heterogeneous Networks.pdf
- Node Density and Delay in Large-Scale Wireless Networks with Unreliable Links.pdf
- Two-Dimensional Route Switching in Cognitive Radio Networks:A Game-Theoretical Framework.pdf
- Two-Dimensional Route Switching in Cognitive Radio Networks:A Game-Theoretical Framework.ppt
- Optimal Secrecy Capacity-Delay Tradeoff in Large-Scale Mobile Ad Hoc Networks.pdf
- Impact of Social Relation and Group Size in Multicast Ad Hoc Networks.pdf
- Impact of Social Relation and Group Size in Multicast Ad Hoc Networks.pptx
- Mobility Weakens the Distinction between Multicast and Unicast.pdf
- Mobility Weakens the Distinction between Multicast and Unicast.pptx
- Are we connected? Optimal Determination of Source-destination Connectivity in Random Networks.pdf
- Asymptotic Analysis on Content Placement and Retrieval in MANETs.pdf
- Connectivity Analysis in Wireless Networks with Correlated Mobility and Cluster Scalability.pdf
- 甘肃农业大学:《VB程序设计基础》课程教学资源(教学大纲)Programming of Visual Basic.pdf
- 甘肃农业大学:《VB程序设计基础》课程教学资源(授课教案)第一章 VB概述.doc
- 甘肃农业大学:《VB程序设计基础》课程教学资源(作业习题)VB习题1.pdf
- 甘肃农业大学:《VB程序设计基础》课程教学资源(PPT讲稿)C语言概述.ppt
- 同济大学:《Visual Basic程序设计简明教程》配套PPT课件讲稿(第三版)第1章 Visual Basic程序设计概述、第2章 VB可视化编程基础、第3章 VB语言基础.ppt
- 同济大学:《Visual Basic程序设计简明教程》配套PPT课件讲稿(第三版)第4章 VB控制结构、第5章 数组和自定义类型、第6章 过程.ppt
- 同济大学:《Visual Basic程序设计简明教程》配套PPT课件讲稿(第三版)第7章 用户界面设计、第8章 数据文件、第9章 图形操作.ppt
- 同济大学:《Visual Basic程序设计简明教程》配套PPT课件讲稿(第三版)第10章 数据库应用基础.ppt
