《计算机网络》课程PPT教学课件(自顶向下方法,英文第三版)第八章 Network Security

Chapter 8 Network Security computer networking James F.Kurose Keith W.Ross A note on the use of these ppt slides: We're making these slides freely available to all (faculty,students,readers). They're in PowerPoint form so you can add,modify,and delete slides (including this one)and slide content to suit your needs.They obviously Computer Networking: represent a lot of work on our part.In return for use,we only ask the following: A Top Down Approach If you use these slides (e.g.,in a class)in substantially unaltered form, Featuring the Internet that you mention their source(after all,we'd like people to use our book!) f you post any slides in substantially unaltered form on a ww site,that 3rd edition. you note that they are adapted from(or perhaps identical to)our slides,and Jim Kurose,Keith Ross note our copyright of this material. Addison-Wesley,July Thanks and enjoy!JFK/KWR 2004. All material copyright 1996-2006 J.F Kurose and K.W.Ross,All Rights Reserved 8:Network Security 8-1
8: Network Security 8-1 Chapter 8 Network Security A note on the use of these ppt slides: We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the following: ❑ If you use these slides (e.g., in a class) in substantially unaltered form, that you mention their source (after all, we’d like people to use our book!) ❑ If you post any slides in substantially unaltered form on a www site, that you note that they are adapted from (or perhaps identical to) our slides, and note our copyright of this material. Thanks and enjoy! JFK/KWR All material copyright 1996-2006 J.F Kurose and K.W. Ross, All Rights Reserved Computer Networking: A Top Down Approach Featuring the Internet, 3rd edition. Jim Kurose, Keith Ross Addison-Wesley, July 2004

Chapter 8:Network Security Chapter goals: understand principles of network security: o cryptography and its many uses beyond "confidentiality" o authentication o message integrity o key distribution Osecurity in practice: o firewalls o security in application,transport,network,link layers 8:Network Security 8-2
8: Network Security 8-2 Chapter 8: Network Security Chapter goals: understand principles of network security: cryptography and its many uses beyond “confidentiality” authentication message integrity key distribution security in practice: firewalls security in application, transport, network, link layers

Chapter 8 roadmap 8.1 What is network security? 8.2 Principles of cryptography 8.3 Authentication 8.4 Integrity 8.5 Key Distribution and certification 8.6 Access control:firewalls 8.7 Attacks and counter measures 8.8 Security in many layers 8:Network Security 8-3
8: Network Security 8-3 Chapter 8 roadmap 8.1 What is network security? 8.2 Principles of cryptography 8.3 Authentication 8.4 Integrity 8.5 Key Distribution and certification 8.6 Access control: firewalls 8.7 Attacks and counter measures 8.8 Security in many layers

What is network security? Confidentiality:only sender,intended receiver should "understand"message contents o sender encrypts message o receiver decrypts message Authentication:sender,receiver want to confirm identity of each other Message Integrity:sender,receiver want to ensure message not altered (in transit,or afterwards) without detection Access and Availability:services must be accessible and available to users 8:Network Security 8-4
8: Network Security 8-4 What is network security? Confidentiality: only sender, intended receiver should “understand” message contents sender encrypts message receiver decrypts message Authentication: sender, receiver want to confirm identity of each other Message Integrity: sender, receiver want to ensure message not altered (in transit, or afterwards) without detection Access and Availability: services must be accessible and available to users
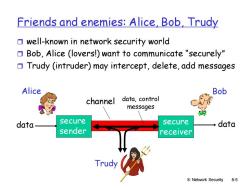
Friends and enemies:Alice,Bob,Trudy well-known in network security world Bob,Alice (lovers!)want to communicate "securely" Trudy (intruder)may intercept,delete,add messages Alice Bob channel data,control messages data secure secure data sender receiver Trudy 8:Network Security 8-5
8: Network Security 8-5 Friends and enemies: Alice, Bob, Trudy well-known in network security world Bob, Alice (lovers!) want to communicate “securely” Trudy (intruder) may intercept, delete, add messages secure sender secure receiver channel data, control messages data data Alice Bob Trudy

Who might Bob,Alice be? .well,real-life Bobs and Alices! Web browser/server for electronic transactions (e.g.,on-line purchases) Oon-line banking client/server DNS servers routers exchanging routing table updates other examples? 8:Network Security 8-6
8: Network Security 8-6 Who might Bob, Alice be? . well, real-life Bobs and Alices! Web browser/server for electronic transactions (e.g., on-line purchases) on-line banking client/server DNS servers routers exchanging routing table updates other examples?

There are bad guys (and girls)out there! Q:What can a "bad guy"do? A:a lot! o eavesdrop:intercept messages o actively insert messages into connection o impersonation:can fake (spoof)source address in packet (or any field in packet) o hijacking:"take over"ongoing connection by removing sender or receiver,inserting himself in place o denial of service:prevent service from being used by others(e.g.,by overloading resources) more on this later. 8:Network Security 8-7
8: Network Security 8-7 There are bad guys (and girls) out there! Q: What can a “bad guy” do? A: a lot! eavesdrop: intercept messages actively insert messages into connection impersonation: can fake (spoof) source address in packet (or any field in packet) hijacking: “take over” ongoing connection by removing sender or receiver, inserting himself in place denial of service: prevent service from being used by others (e.g., by overloading resources) more on this later

Chapter 8 roadmap 8.1 What is network security? 8.2 Principles of cryptography 8.3 Authentication 8.4 Integrity 8.5 Key Distribution and certification 8.6 Access control:firewalls 8.7 Attacks and counter measures 8.8 Security in many layers 8:Network Security 8-8
8: Network Security 8-8 Chapter 8 roadmap 8.1 What is network security? 8.2 Principles of cryptography 8.3 Authentication 8.4 Integrity 8.5 Key Distribution and certification 8.6 Access control: firewalls 8.7 Attacks and counter measures 8.8 Security in many layers

The language of cryptography ⑥学Alice's ⑥学Bob's encryption K decryption key B key plaintext encryption ciphertext decryption plaintext algorithm algorithm symmetric key crypto:sender,receiver keys identical public-key crypto:encryption key public,decryption key secret (private) 8:Network Security 8-9
8: Network Security 8-9 The language of cryptography symmetric key crypto: sender, receiver keys identical public-key crypto: encryption key public, decryption key secret (private) plaintext ciphertext plaintext K A encryption algorithm decryption algorithm Alice’s encryption key Bob’s decryption key K B

Symmetric key cryptography substitution cipher:substituting one thing for another o monoalphabetic cipher:substitute one letter for another plaintext:abcdefghijklmnopqrstuvwxyz ciphertext:mnbvcxzasdfghjklpoiuytrewq E.g.:plaintext:bob.i love you.alice ciphertext:nkn.s gktc wky.mgsbc Q:How hard to break this simple cipher?: brute force (how hard?) ▣other? 8:Network Security 8-10
8: Network Security 8-10 Symmetric key cryptography substitution cipher: substituting one thing for another monoalphabetic cipher: substitute one letter for another plaintext: abcdefghijklmnopqrstuvwxyz ciphertext: mnbvcxzasdfghjklpoiuytrewq Plaintext: bob. i love you. alice ciphertext: nkn. s gktc wky. mgsbc E.g.: Q: How hard to break this simple cipher?: ❑ brute force (how hard?) ❑ other?
按次数下载不扣除下载券;
注册用户24小时内重复下载只扣除一次;
顺序:VIP每日次数-->可用次数-->下载券;
- 《计算机网络》课程PPT教学课件(自顶向下方法,英文第三版)第九章 Network Management.ppt
- 《计算机网络》课程PPT教学课件(自顶向下方法,英文第三版)第四章 Network Layer.ppt
- 《计算机网络》课程PPT教学课件(自顶向下方法,英文第三版)第六章 Wireless and Mobile Networks.ppt
- 《计算机网络》课程PPT教学课件(自顶向下方法,英文第三版)第五章 Link Layer and LANs.ppt
- 《计算机网络》课程PPT教学课件(自顶向下方法,英文第三版)第二章 Application Layer.ppt
- 《计算机网络》课程PPT教学课件(自顶向下方法,英文第三版)第三章 Transport Layer.ppt
- 《计算机网络》课程PPT教学课件(自顶向下方法,英文第三版)第七章 Multimedia Networking.ppt
- 《计算机网络》课程PPT教学课件(自顶向下方法,英文第三版)第一章 Computer Networks and the Internet.ppt
- 《计算机网络》课程教学大纲(供四年制计算机科学与技术本科专业使用).pdf
- 《计算机网络》课程授课教案(双语,计算机科学与技术专业).doc
- 《网页制作》课程教学资源(讲义)第四章.doc
- 《网页制作》课程教学资源(讲义)第十章.doc
- 《网页制作》课程教学资源(讲义)第十一章.doc
- 《网页制作》课程教学资源(讲义)第六章.doc
- 《网页制作》课程教学资源(讲义)第八章.doc
- 《网页制作》课程教学资源(讲义)第五章.doc
- 《网页制作》课程教学资源(讲义)第九章.doc
- 《网页制作》课程教学资源(讲义)第三章.doc
- 《网页制作》课程教学资源(讲义)第七章.doc
- 《网页制作》课程教学资源(讲义)第一章和第二章(石河子大学:李伟).doc
- 《计算机网络》课程PPT教学课件(自顶向下方法,中文第三版)第一章 计算机网络和因特网概述.ppt
- 《计算机网络》课程PPT教学课件(自顶向下方法,中文第三版)第三章 运输层.ppt
- 《计算机网络》课程PPT教学课件(自顶向下方法,中文第三版)第二章 应用层.ppt
- 《计算机网络》课程PPT教学课件(自顶向下方法,中文第三版)第五章 链路层与局域网.ppt
- 《计算机网络》课程PPT教学课件(自顶向下方法,中文第三版)第六章 无线网和移动网.ppt
- 《计算机网络》课程PPT教学课件(自顶向下方法,中文第三版)第四章 网络层.ppt
- 《计算机网络》课程PPT教学课件(自顶向下方法,中文第三版)第七章 多媒体联网.ppt
- 《计算机网络》课程PPT教学课件(自顶向下方法,中文第三版)第九章 网络管理.ppt
- 《计算机网络》课程PPT教学课件(自顶向下方法,中文第三版)第八章 网络安全.ppt
- 《The Basics of Information Security》参考书籍PDF电子版(Understanding the Fundamentals of InfoSec in Theory and Practice,作者:Jason Andress).pdf
- 华南农业大学:《高级语言程序设计》课程授课教案(负责人:刘财兴).pdf
- 华南农业大学:《高级语言程序设计》课程教学大纲 Programming.pdf
- 华南农业大学:《高级语言程序设计》课程教学资源(PPT课件)chap01_概论.ppt
- 华南农业大学:《高级语言程序设计》课程教学资源(PPT课件)chap02_用C语言编写程序.ppt
- 华南农业大学:《高级语言程序设计》课程教学资源(PPT课件)chap03_分支结构.ppt
- 华南农业大学:《高级语言程序设计》课程教学资源(PPT课件)chap04_循环结构.ppt
- 华南农业大学:《高级语言程序设计》课程教学资源(PPT课件)chap05_函数.ppt
- 华南农业大学:《高级语言程序设计》课程教学资源(PPT课件)chap06_回顾数据类型和表达式.ppt
- 华南农业大学:《高级语言程序设计》课程教学资源(PPT课件)chap07_数组.ppt
- 华南农业大学:《高级语言程序设计》课程教学资源(PPT课件)chap08_指针.ppt
