《计算机网络 Computer Networking》课程PPT教学课件(A Top Down Approach,8th edition)Chapter 8 Security in Computer Networks

Chapter 8 James F.Kurose Keith W.Ross Security A note on the use of these PowerPoint slides: We're making these slides freely available to all(faculty,students, readers).They're in PowerPoint form so you see the animations;and can add,modify,and delete slides (including this one)and slide content to suit your needs.They obviously represent a lot of work on our part. COMPUTER In return for use,we only ask the following: NETWORKING If you use these slides(e.g.,in a class)that you mention their A TOP-DOWN APPROACH source(after all,we'd like people to use our book!) If you postany slides on a www site,that you note that they are adapted from(or perhaps identical to)our slides,and note our copyright of this material. Computer Networking:A For a revision history,see the slide note for this page. Top-Down Approach Thanks and enjoy!JFK/KWR 8th edition All material copyright 1996-2020 Jim Kurose,Keith Ross J.F Kurose and K.W.Ross,All Rights Reserved Pearson,2020
Computer Networking: A Top-Down Approach 8 th edition Jim Kurose, Keith Ross Pearson, 2020 Chapter 8 Security A note on the use of these PowerPoint slides: We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you see the animations; and can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the following: ▪ If you use these slides (e.g., in a class) that you mention their source (after all, we’d like people to use our book!) ▪ If you post any slides on a www site, that you note that they are adapted from (or perhaps identical to) our slides, and note our copyright of this material. For a revision history, see the slide note for this page. Thanks and enjoy! JFK/KWR All material copyright 1996-2020 J.F Kurose and K.W. Ross, All Rights Reserved

Security:overview Chapter goals: understand principles of network security: cryptography and its many uses beyond"confidentiality" ·authentication ·message integrity security in practice: firewalls and intrusion detection systems security in application,transport,network,link layers Security:8-2
Security: overview Security: 8- 2 Chapter goals: ▪ understand principles of network security: • cryptography and its many uses beyond “confidentiality” • authentication • message integrity ▪ security in practice: • firewalls and intrusion detection systems • security in application, transport, network, link layers

Chapter 8 outline -What is network security? Principles of cryptography Message integrity,authentication ■Securing e-mail Securing TCP connections:TLS Network layer security:IPsec -Security in wireless and mobile networks Operational security:firewalls and IDS Security:8-3
Chapter 8 outline ▪What is network security? ▪ Principles of cryptography ▪ Message integrity, authentication ▪ Securing e-mail ▪ Securing TCP connections: TLS ▪ Network layer security: IPsec ▪ Security in wireless and mobile networks ▪Operational security: firewalls and IDS Security: 8- 3

What is network security? confidentiality:only sender,intended receiver should "understand" message contents sender encrypts message receiver decrypts message authentication:sender,receiver want to confirm identity of each other message integrity:sender,receiver want to ensure message not altered (in transit,or afterwards)without detection access and availability:services must be accessible and available to users Security:8-4
What is network security? Security: 8- 4 confidentiality: only sender, intended receiver should “understand” message contents • sender encrypts message • receiver decrypts message authentication: sender, receiver want to confirm identity of each other message integrity: sender, receiver want to ensure message not altered (in transit, or afterwards) without detection access and availability: services must be accessible and available to users

Friends and enemies:Alice,Bob,Trudy well-known in network security world Bob,Alice(lovers!)want to communicate "securely" Trudy(intruder)may intercept,delete,add messages Alice channel data,control Bob messages secure secure data- data sender receiver Trudy Security:8-5
Friends and enemies: Alice, Bob, Trudy Security: 8- 5 ▪ well-known in network security world ▪ Bob, Alice (lovers!) want to communicate “securely” ▪ Trudy (intruder) may intercept, delete, add messages secure sender secure receiver channel data, control messages data data Alice Bob Trudy

Friends and enemies:Alice,Bob,Trudy Who might Bob and Alice be? ..well,real-life Bobs and Alices! Web browser/server for electronic transactions(e.g.,on-line purchases) on-line banking client/server ■DNS servers BGP routers exchanging routing table updates ■other examples?
Friends and enemies: Alice, Bob, Trudy Who might Bob and Alice be? ▪ … well, real-life Bobs and Alices! ▪ Web browser/server for electronic transactions (e.g., on-line purchases) ▪ on-line banking client/server ▪ DNS servers ▪ BGP routers exchanging routing table updates ▪ other examples?

There are bad guys(and girls)out therel Q:What can a"bad guy"do? A:A lot!(recall section 1.6) eavesdrop:intercept messages actively insert messages into connection impersonation:can fake(spoof)source address in packet (or any field in packet) hijacking:"take over"ongoing connection by removing sender or receiver,inserting himself in place denial of service:prevent service from being used by others(e.g., by overloading resources)
There are bad guys (and girls) out there! Q: What can a “bad guy” do? A: A lot! (recall section 1.6) • eavesdrop: intercept messages • actively insert messages into connection • impersonation: can fake (spoof) source address in packet (or any field in packet) • hijacking: “take over” ongoing connection by removing sender or receiver, inserting himself in place • denial of service: prevent service from being used by others (e.g., by overloading resources)

Chapter 8 outline What is network security? Principles of cryptography Message integrity,authentication Securing e-mail Securing TCP connections:TLS Network layer security:IPsec -Security in wireless and mobile networks -Operational security:firewalls and IDS Security:8-8
Chapter 8 outline ▪ What is network security? ▪ Principles of cryptography ▪ Message integrity, authentication ▪ Securing e-mail ▪ Securing TCP connections: TLS ▪ Network layer security: IPsec ▪ Security in wireless and mobile networks ▪Operational security: firewalls and IDS Security: 8- 8

The language of cryptography @→Alice's @学Bob's KA encryption decryption key key plaintext encryption ciphertext decryption plaintext algorithm algorithm m:plaintext message KA(m):ciphertext,encrypted with key KA m KB(KA(m)) Security:8-9
The language of cryptography m: plaintext message KA (m): ciphertext, encrypted with key KA m = KB (KA (m)) plaintext ciphertext plaintext KA encryption algorithm decryption algorithm Alice’s encryption key Bob’s decryption key KB Security: 8- 9
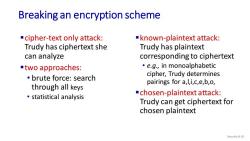
Breaking an encryption scheme cipher-text only attack: known-plaintext attack: Trudy has ciphertext she Trudy has plaintext can analyze corresponding to ciphertext two approaches: e.g.,in monoalphabetic cipher,Trudy determines 。brute force:search pairings for a,l,i,c,e,b,o, through all keys statistical analysis chosen-plaintext attack: Trudy can get ciphertext for chosen plaintext Security:8-10
Breaking an encryption scheme ▪cipher-text only attack: Trudy has ciphertext she can analyze ▪two approaches: • brute force: search through all keys • statistical analysis ▪known-plaintext attack: Trudy has plaintext corresponding to ciphertext • e.g., in monoalphabetic cipher, Trudy determines pairings for a,l,i,c,e,b,o, ▪chosen-plaintext attack: Trudy can get ciphertext for chosen plaintext Security: 8- 10
按次数下载不扣除下载券;
注册用户24小时内重复下载只扣除一次;
顺序:VIP每日次数-->可用次数-->下载券;
- 《计算机网络 Computer Networking》课程PPT教学课件(A Top Down Approach,8th edition)Chapter 7 Wireless and Mobile Networks.pptx
- 《计算机网络 Computer Networking》课程PPT教学课件(A Top Down Approach,8th edition)Chapter 6 Link Layer and LANs.pptx
- 《计算机网络 Computer Networking》课程PPT教学课件(A Top Down Approach,8th edition)Chapter 5 The Network Layer - Control Plane.pptx
- 《计算机网络 Computer Networking》课程PPT教学课件(A Top Down Approach,8th edition)Chapter 4 The Network Layer - Data Plane.pptx
- 《计算机网络 Computer Networking》课程PPT教学课件(A Top Down Approach,8th edition)Chapter 3 Transport Layer.pptx
- 《计算机网络 Computer Networking》课程PPT教学课件(A Top Down Approach,8th edition)Chapter 2 Application Layer.pptx
- 《计算机网络 Computer Networking》课程PPT教学课件(A Top Down Approach,8th edition)Chapter 1 Computer Networks and the Internet.pptx
- 《计算机网络 Computer Networking》课程PPT教学课件(A Top Down Approach,7th edition)Chapter 9 Multimedia Networking.pptx
- 《计算机网络 Computer Networking》课程PPT教学课件(A Top Down Approach,7th edition)Chapter 8 Security in Computer Networks.pptx
- 《计算机网络 Computer Networking》课程PPT教学课件(A Top Down Approach,7th edition)Chapter 7 Wireless and Mobile Networks.pptx
- 《计算机网络 Computer Networking》课程PPT教学课件(A Top Down Approach,7th edition)Chapter 6 Link Layer and LANs.pptx
- 《计算机网络 Computer Networking》课程PPT教学课件(A Top Down Approach,7th edition)Chapter 5 The Network Layer - Control Plane.pptx
- 《计算机网络 Computer Networking》课程PPT教学课件(A Top Down Approach,7th edition)Chapter 4 The Network Layer - Data Plane.ppt
- 《计算机网络 Computer Networking》课程PPT教学课件(A Top Down Approach,7th edition)Chapter 3 Transport Layer.ppt
- 《计算机网络 Computer Networking》课程PPT教学课件(A Top Down Approach,7th edition)Chapter 2 Application Layer.ppt
- 《计算机网络 Computer Networking》课程PPT教学课件(A Top Down Approach,7th edition)Chapter 1 Computer Networks and the Internet.ppt
- 《计算机网络 Computer Networking》课程教学课件(A Top Down Approach,6th edition)Chapter 9 Network Management.pdf
- 《计算机网络 Computer Networking》课程教学课件(A Top Down Approach,6th edition)Chapter 8 Security.pdf
- 《计算机网络 Computer Networking》课程教学课件(A Top Down Approach,6th edition)Chapter 7 Multimedia Networking.pdf
- 《计算机网络 Computer Networking》课程课程实验讲稿(Wireshark Lab,6th edition)Analyze NAT with Wireshark.pdf
- 陕西师范大学:《计算机网络 Computer Networking》课程教学资源(习题指导)计算机网络课后习题指导(A Top-down Approach,6th edition).pdf
- 《计算机网络 Computer Networking》课程课程实验讲稿(Wireshark Lab,8th edition)01 Getting Started Wireshark.pdf
- 《计算机网络 Computer Networking》课程课程实验讲稿(Wireshark Lab,8th edition)02 Analyze HTTP with Wireshark.pdf
- 《计算机网络 Computer Networking》课程课程实验讲稿(Wireshark Lab,8th edition)03 Analyze DNS with Wireshark.pdf
- 《计算机网络 Computer Networking》课程课程实验讲稿(Wireshark Lab,8th edition)04 Analyze UDP with Wireshark.pdf
- 《计算机网络 Computer Networking》课程课程实验讲稿(Wireshark Lab,8th edition)05 Analyze TCP with Wireshark.pdf
- 《计算机网络 Computer Networking》课程课程实验讲稿(Wireshark Lab,8th edition)06 Analyze IP with Wireshark.pdf
- 《计算机网络 Computer Networking》课程课程实验讲稿(Wireshark Lab,8th edition)07 Analyze ICMP with Wireshark.pdf
- 《计算机网络 Computer Networking》课程课程实验讲稿(Wireshark Lab,8th edition)08 Analyze DHCP with Wireshark.pdf
- 《计算机网络 Computer Networking》课程课程实验讲稿(Wireshark Lab,8th edition)09 Analyze NAT with Wireshark.pdf
- 《计算机网络 Computer Networking》课程课程实验讲稿(Wireshark Lab,8th edition)10 Analyze ARP with Wireshark.pdf
- 《计算机网络》课程教学资源(参考资料)交换机路由器技术资料大全.doc
- 中华人民共和国通信行业标准:千兆比以太网交换机设备技术规范(YD/T 1099—2001)Technical Specification for Giga Bit Ethernet LAN Switch Equipment.pdf
- 石河子大学:《计算机网络》课程教学资源(大纲教案,打印版)课程教学大纲 Computer Network(2013版).pdf
- 石河子大学:《计算机网络》课程教学资源(大纲教案,打印版)课程设计教学大纲(2013版)计算机网络工程技术实践.pdf
- 石河子大学:《计算机网络》课程教学资源(大纲教案)课程设计教学大纲(20161版).doc
- 石河子大学:《计算机网络》课程教学资源(大纲教案)课程考试大纲(2016版).doc
- 石河子大学:《计算机网络》课程教学资源(大纲教案)课程实验大纲(2016版).doc
- 石河子大学:《计算机网络》课程教学资源(大纲教案)课程教学大纲(2016版).doc
- 石河子大学:《计算机网络》课程教学资源(大纲教案,打印版)课程设计教学大纲(2019版).pdf
