西安电子科技大学:《软件定义联网与虚拟化》课程教学资源(PPT课件)On the Safety of IoT Device Physical Interaction Control

On the Safety of loT Device Physical Interaction Control 成员:闫坤、陈晨洋、李秉坤
成员:闫坤、陈晨洋、李秉坤 On the Safety of IoT Device Physical Interaction Control

Outline 1.Research Background >2.System Implementation >3.Experiment and Results >4.Sum and Prospect 1
Outline ➢ 1. Research Background ➢ 2. System Implementation ➢ 3. Experiment and Results ➢ 4. Sum and Prospect 1

Research Background Existing research focuses on solving traditional problems in the Internet of Things environment 1.Device firmware error 2.Communication protocol vulnerability 3.Malware attack 4.System design flaws 2
Research Background Existing research focuses on solving traditional problems in the Internet of Things environment : 1. Device firmware error 2. Communication protocol vulnerability 3. Malware attack 4. System design flaws 2
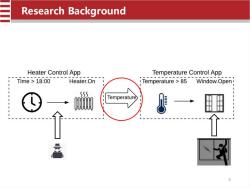
Research Background Heater Control App Temperature Control App Time>18:00 Heater.On Temperature >85 Window.Open 1 555 Temperature 3
Research Background 3

Research Background loTMon:Research loT devices interacting with the surrounding environment through physical channels 1.Discover any possible physical interactions between loT devices 2.Generate all potential interaction chains between applications in the loT environment 3.Assess the security risks of the interaction chain between each discovered application based on physical impact 4
Research Background IoTMon: Research IoT devices interacting with the surrounding environment through physical channels 1. Discover any possible physical interactions between IoT devices 2. Generate all potential interaction chains between applications in the IoT environment 3. Assess the security risks of the interaction chain between each discovered application based on physical impact 4

System Implementation Application Analysis Interaction Chain Discovery Risk Analysis Mitigation Chains Code Intra-app Intra-app Behavior Modeling Analysis Interactions Clustering Inter-app Applications Interaction Chain Generation Risk Evaluation Physical Physical Description Channel Identification Channels Risk Mitigation
System Implementation 5
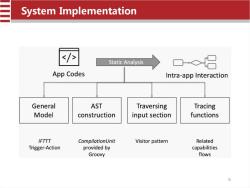
System Implementation Static Analysis 口◇ App Codes Intra-app Interaction General AST Traversing Tracing Model construction input section functions IFTTT CompilationUnit Visitor pattern Related Trigger-Action provided by capabilities Groovy flows 6
System Implementation 6
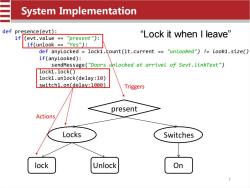
System Implementation def presence(evt): if (evt.value ="present"): "Lock it when I leave” if(unlook ="Yes"): def anyLocked lock1.count(it.current ="unlooked")!=Look1.size() if(anyLooked): sendMessage("Doors unlocked at arrivel of Sevt.LinkText") lock1.lock() lock1.unlock(delay:10) switch1.on(delay:1000) Triggers present Actions Locks Switches lock Unlock On 7
System Implementation def presence(evt): if (evt.value == "present"): if(unlook == "Yes"): def anyLocked = lock1.count(it.current == "unlooked") != look1.size() if(anyLooked): sendMessage("Doors unlocked at arrivel of Sevt.linkText") lock1.lock() lock1.unlock(delay:10) switch1.on(delay:1000) “Lock it when I leave” Triggers present Locks Switches lock Unlock On Actions 7
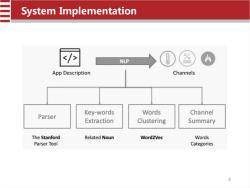
System Implementation 7 NLP App Description Channels Key-words Words Channel Parser Extraction Clustering Summary The Stanford Related Noun Word2Vec Words Parser Tool Categories 8
System Implementation 8
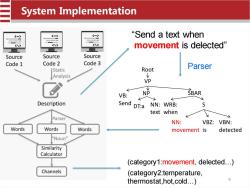
System Implementation “Send a text when movement is delected" Source Source Source Code 1 Code 2 Code 3 Root Parser Static Analysis VP V VB: NP SBAR Description Send DT:a NN:WRB: s text when Parser NN: VBZ:VBN: Words Words Words movement is detected "Noun" Similarity Calculator (category1:movement,delected...) Channels (category2:temperature, thermostat,hot,cold...) 9
“Send a text when movement is delected” NP VP VB: Send Root SBAR DT:a NN: text WRB: when S NN: movement VBZ: is VBN: detected Parser (category1:movement, delected…) (category2:temperature, thermostat,hot,cold…) System Implementation 9
按次数下载不扣除下载券;
注册用户24小时内重复下载只扣除一次;
顺序:VIP每日次数-->可用次数-->下载券;
- 西安电子科技大学:《软件定义联网与虚拟化》课程教学资源(PPT课件)Intelligent Home Network and Technology.ppsm
- 西安电子科技大学:《软件定义联网与虚拟化》课程教学资源(课件讲稿)Ch3 -Network function virtualization.pdf
- 西安电子科技大学:《软件定义联网与虚拟化》课程教学资源(课件讲稿)Ch2 -software defined networking.pdf
- 西安电子科技大学:《软件定义联网与虚拟化》课程教学资源(课件讲稿)Ch1 -networking basics and trend.pdf
- Peer-to-peer information systems:concepts and models, state-of-the-art, and future systems.pdf
- 烟台理工学院:《计算机控制系统》课程教学大纲 Computer Control System.doc
- 烟台理工学院:《计算机控制系统课程设计》课程教学大纲 Course Design of Computer Control.doc
- 烟台理工学院:《神经网络与深度学习》教学大纲.doc
- 烟台理工学院:《深度学习课程设计》教学大纲.doc
- 烟台理工学院:《人工智能原理》课程教学资源(教学大纲)Principles of Artificial Intelligence(人工智能专业本科大二).doc
- 烟台理工学院:《人工智能编程技术》课程教学资源(教学大纲)Course Design of artificial intelligence program technology.doc
- 烟台理工学院:《Python程序设计》课程教学资源(教学大纲)Course Design of Python(人工智能专业本科大二).doc
- 烟台理工学院:《Python程序设计》课程教学资源(教学大纲)理论课教学大纲(自动化和机器人工程专业大一本科、人工智能专业大二本科).docx
- 川北医学院:《单片机原理》课程教学资源(讲义)第9章 串行扩展技术.pdf
- 川北医学院:《单片机原理》课程教学资源(讲义)第8章 串行通信.pdf
- 川北医学院:《单片机原理》课程教学资源(讲义)第7章 并行扩展技术.pdf
- 川北医学院:《单片机原理》课程教学资源(讲义)第6章 定时器/计数器.pdf
- 川北医学院:《单片机原理》课程教学资源(讲义)第5章 中断系统.pdf
- 川北医学院:《单片机原理》课程教学资源(讲义)第4章 汇编语言程序设计.pdf
- 川北医学院:《单片机原理》课程教学资源(讲义)第3章 8051指令系统.pdf
- 西安电子科技大学:《软件定义联网与虚拟化》课程教学资源(PPT课件)5G Networking.ppsm
- 西安电子科技大学:《软件定义联网与虚拟化》课程教学资源(PPT课件)网络软件化 Overview of Network Softwarization and its Core Technologies.ppsm
- 西安电子科技大学:《接入网新技术》课程教学资源(PPT课件)课程介绍(宽带通信网技术 Broadband Communication Networking Technologies).pptx
- 西安电子科技大学:《接入网新技术》课程教学资源(PPT课件)第一章 信息网与接入网概论.pptx
- 西安电子科技大学:《接入网新技术》课程教学资源(PPT课件)第一章 宽带ATM技术.ppt
- 西安电子科技大学:《接入网新技术》课程教学资源(PPT课件)第二章 xDSL技术.ppt
- 中国科学技术大学:《数据结构及其算法》课程教学资源(课件讲稿)Ch1 绪论(主讲:肖明军).pdf
- 中国科学技术大学:《数据结构及其算法》课程教学资源(课件讲稿)Ch2 线性表.pdf
- 中国科学技术大学:《数据结构及其算法》课程教学资源(课件讲稿)Ch3 栈和队列.pdf
- 中国科学技术大学:《数据结构及其算法》课程教学资源(课件讲稿)Ch4 串.pdf
- 中国科学技术大学:《数据结构及其算法》课程教学资源(课件讲稿)Ch5 数组和广义表.pdf
- 中国科学技术大学:《数据结构及其算法》课程教学资源(课件讲稿)Ch6 树.pdf
- 中国科学技术大学:《数据结构及其算法》课程教学资源(课件讲稿)Ch7 图(1/3).pdf
- 中国科学技术大学:《数据结构及其算法》课程教学资源(课件讲稿)Ch7 图(2/3).pdf
- 中国科学技术大学:《数据结构及其算法》课程教学资源(课件讲稿)Ch7 图(3/3).pdf
- 中国科学技术大学:《数据结构及其算法》课程教学资源(课件讲稿)Ch9 查找(1/2).pdf
- 中国科学技术大学:《数据结构及其算法》课程教学资源(课件讲稿)Ch9 查找(2/2).pdf
- 中国科学技术大学:《数据结构及其算法》课程教学资源(课件讲稿)Ch10 排序(1/2).pdf
- 中国科学技术大学:《数据结构及其算法》课程教学资源(课件讲稿)Ch10 排序(2/2).pdf
- 中国科学技术大学:《网络信息安全 NETWORK SECURITY》课程教学资源(PPT课件讲稿)第一章 计算机网络安全概述1/2(主讲:肖明军、席菁).ppt
