Efficient and Precise Points-to Analysis:Modeling the Heap by Merging Equivalent Automata

● Efficient and Precise Points-to Analysis: Modeling the Heap by Merging Equivalent Automata Tian Tan,Yue Li and Jingling Xue PLDI 2017 UNSW June,2017 SYDNEY
Efficient and Precise Points-to Analysis: Modeling the Heap by Merging Equivalent Automata Tian Tan, Yue Li and Jingling Xue PLDI 2017 June, 2017 1

A New Points-to Analysis Technique for Object-Oriented Programs 2
A New Points-to Analysis Technique for Object-Oriented Programs 2

Points-to Analysis ●Determines 。“which objects a variable can point to, 3
Points-to Analysis Determines ◦ “which objects a variable can point to?” 3
Uses of Points-to Analysis Clients Tools ●Security analysis Bug detection Soot DroidSafe Compiler optimization Program verification ①OOP专Chord Program understanding WALA T.3.WATSON UBRARIES FOR ANALYSIS ●0● 4
Uses of Points-to Analysis Clients Tools Security analysis Bug detection Compiler optimization Program verification Program understanding … Chord 4 …
Uses of Points-to Analysis Clients Tools ●Security analysis ·Bug detection Soot DroidSafe Compiler optimization Program verification ①OOP专Chord Program understanding WALA T.3.WATSON UBRARIES FOR ANALYSIS ●0● Call Graph 5
Uses of Points-to Analysis Clients Tools Security analysis Bug detection Compiler optimization Program verification Program understanding … Chord 5 … Call Graph

Existing Call Graph Construction On-the-fly construction (run with points-to analysis) o Precise o Inefficient 6
Existing Call Graph Construction 6 On-the-fly construction (run with points-to analysis) ◦ Precise ◦ Inefficient

Existing Call Graph Construction On-the-fly construction (run with points-to analysis) o Precise o Inefficient 3-object-sensitive points-to analysis o Very precise Adopted by.e.g.DOOP DroidSafe 有Chord 7
Existing Call Graph Construction 7 On-the-fly construction (run with points-to analysis) ◦ Precise ◦ Inefficient 3-object-sensitive points-to analysis ◦ Very precise ◦ Adopted by, e.g., 7 Chord

3-Object-Sensitive Points-to Analysis Analyze Java programs DOOP Intel Xeon E5 3.70GHz,128GB of memory Time budget:5 hours (18000 secs) 8
3-Object-Sensitive Points-to Analysis Analyze Java programs ◦ Intel Xeon E5 3.70GHz,128GB of memory ◦ Time budget: 5 hours (18000 secs) 8
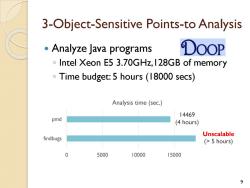
3-Object-Sensitive Points-to Analysis Analyze Java programs DOOP Intel Xeon E5 3.70GHz,128GB of memory Time budget:5 hours (18000 secs) Analysis time(sec.) 14469 pmd (4 hours) Unscalable findbugs (>5 hours) 0 5000 10000 15000 9
3-Object-Sensitive Points-to Analysis Analyze Java programs ◦ Intel Xeon E5 3.70GHz,128GB of memory ◦ Time budget: 5 hours (18000 secs) 9 Unscalable (> 5 hours) 14469 (4 hours) 0 5000 10000 15000 findbugs pmd Analysis time (sec.)

Two Mainstreams of Points-to Analysis Techniques ●Model control-flow ●Model data-flow 10
Two Mainstreams of Points-to Analysis Techniques Model control-flow Model data-flow 10
按次数下载不扣除下载券;
注册用户24小时内重复下载只扣除一次;
顺序:VIP每日次数-->可用次数-->下载券;
- Making k-Object-Sensitive Pointer Analysis More Precise with Still k-Limiting.pdf
- Efficient and Precise Points-to Analysis:Modeling the Heap by Merging Equivalent Automata.pdf
- Precise and Efficient Points-to Analysis via New Context-Sensitivity and Heap Abstraction.pdf
- Reflection Analysis for Java:Uncovering More Reflective Targets Precisely.pdf
- Scalability-First Pointer Analysis with Self-Tuning Context-Sensitivity.pdf
- Precision-Guided Context Sensitivity for Pointer Analysis.pdf
- Understanding and Analyzing Java Reflection.pdf
- A Principled Approach to Selective Context Sensitivity for Pointer Analysis.pdf
- Making Pointer Analysis More Precise by Unleashing the Power of Selective Context Sensitivity.pdf
- 《无线互联网 Principles of Wireless Networking》课程教学资源(阅读材料)基于SDN的移动网络中可扩展的感知用户体验的路径选择.pdf
- 《无线互联网 Principles of Wireless Networking》课程教学资源(阅读材料)适用于5G毫米波车载通信的机器学习算法.pdf
- 电子科技大学:《无线互联网 Principles of Wireless Networking》课程教学资源(课件讲稿)Handout 06 DL for MEC.pdf
- 电子科技大学:《无线互联网 Principles of Wireless Networking》课程教学资源(课件讲稿)Handout 05-2 Random Access.pdf
- 电子科技大学:《无线互联网 Principles of Wireless Networking》课程教学资源(课件讲稿)Handout 05-1 Random Access.pdf
- 电子科技大学:《无线互联网 Principles of Wireless Networking》课程教学资源(课件讲稿)Handout 04-2 OFDMA-TDMA Cellular.pdf
- 电子科技大学:《无线互联网 Principles of Wireless Networking》课程教学资源(课件讲稿)Handout 04-1 OFDMA-TDMA Cellular.pdf
- 电子科技大学:《无线互联网 Principles of Wireless Networking》课程教学资源(课件讲稿)Handout 03 Cellular CDMA.pdf
- 电子科技大学:《无线互联网 Principles of Wireless Networking》课程教学资源(课件讲稿)Handout 02 FDM-TDMA Cellular.pdf
- 电子科技大学:《无线互联网 Principles of Wireless Networking》课程教学资源(课件讲稿)Handout 01 INTRODUCTION(王晟).pdf
- 电子科技大学:《计算神经科学》课程教学课件(讲稿)计算神经科学 Computational Neuroscience(共八章,打印版).pdf
- Making k-Object-Sensitive Pointer Analysis More Precise with Still k-Limiting.pdf
- Program Tailoring:Slicing by Sequential Criteria.pdf
- Effective Soundness-Guided Reflection Analysis.pdf
- Self-Inferencing Reflection Resolution for Java.pdf
- 电子科技大学:《UNIX/Linux操作系统内核结构 unix/linux kernel structure》课程教学资源(课件讲稿)第一章 系统概貌(刘玓).pdf
- 电子科技大学:《UNIX/Linux操作系统内核结构 unix/linux kernel structure》课程教学资源(课件讲稿)第二章 核心导言.pdf
- 电子科技大学:《UNIX/Linux操作系统内核结构 unix/linux kernel structure》课程教学资源(课件讲稿)第三章 数据缓冲区高速缓冲.pdf
- 电子科技大学:《UNIX/Linux操作系统内核结构 unix/linux kernel structure》课程教学资源(课件讲稿)第四章 文件和文件系统的内部结构.pdf
- 电子科技大学:《UNIX/Linux操作系统内核结构 unix/linux kernel structure》课程教学资源(课件讲稿)第五章 文件系统的系统调用.pdf
- 电子科技大学:《UNIX/Linux操作系统内核结构 unix/linux kernel structure》课程教学资源(课件讲稿)第六章 进程结构.pdf
- 电子科技大学:《UNIX/Linux操作系统内核结构 unix/linux kernel structure》课程教学资源(课件讲稿)第七章 进程控制.pdf
- 电子科技大学:《UNIX/Linux操作系统内核结构 unix/linux kernel structure》课程教学资源(课件讲稿)第八章 进程调度和时间.pdf
- 电子科技大学:《UNIX/Linux操作系统内核结构 unix/linux kernel structure》课程教学资源(课件讲稿)第九章 输入/输出子系统.pdf
- Automatic Self-Validation for Code Coverage Profilers.pdf
- Hunting for Bugs in Code Coverage Tools via Randomized Differential Testing.pdf
- Effort-Aware Just-in-Time Defect Prediction:Simple Unsupervised Models Could Be Better Than Supervised Models.pdf
- An Empirical Study on Dependence Clusters for Effort-Aware Fault-Proneness Prediction.pdf
- Are Slice-Based Cohesion Metrics Actually Useful in Effort-Aware Post-Release Fault-Proneness Prediction? An Empirical Study.pdf
- 南京大学:《数据库概论 Introduction to Databases》课程教学资源(教学大纲,胡伟).pdf
- 高等教育出版社:《数据库系统实用教程》教材PDF电子版(2006,徐洁磐、柏文阳、刘奇志).pdf
